Vuppula Roopa and Himansu Shekhar Pradhan
Exploring Blockchain and Artificial Intelligence for Next Generation Wireless Networks
Abstract: Future wireless communication networks are exploring the 0.1 to 10 terahertz (THz) band, which presents opportunities for creative usage. However, the management of growing privacy and security issues while allocating resources efficiently to support many devices is a critical activity. Complicated technology affects resource allocation (RA) and network management as it permeates devices and infrastructure. Upgrading from fifthgeneration (5G) to next-generation represents breakthroughs in ultra-low latency, fast data speeds, and artificial intelligence (AI) integration for innovative services and applications. However, these developments convey the challenges that include data processing, RA, network administration, and privacy. Integrating blockchain (BC) as well as machine learning (ML) is a potential alternative to tackle these challenges. This paper presents a comprehensive review, which explores their combined contributions to trust, decentralization, and network security in ML decisions, immutability, and streamlined model sharing. Moreover, it delves into various areas such as rate splitting, next-generation radaroriented communication, BC-oriented spectrum reframing, reconfigurable intelligent surfaces (RIS), and integrated sensing and communication. In addition, it investigates using ML and BC in emerging next-generation communication technologies, which include semantic, molecular, and holographic communications. Finally, the authors deal with the essential unsolved issues, challenges, prospective solutions, and the wide range of opportunities for additional research in this rapidly evolving fields.
Keywords: Artificial intelligence (AI) , blockchain (BC) , machine learning (ML) , resource allocation (RA) , terahertz (THz) communication
I. INTRODUCTION
THE seamless amalgamation of machine learning (ML), decentralization, as well as security is still unsolved, even as fifth-generation (5G) technology goes into the commercialization and activation phases. Conversely, the upcoming sixth generation (next generation) aims to comprehensively integrate ML within a decentralized and highly secure network infrastructure. next generation’s objectives encompass supporting peak data rates, seamless communication, enhanced quality of service and experience (QoSE), seamless communication, increased network capacity, energy and spectrum efficacy, elevated user connectivity, improved system throughput, ultralow latency, high mobility as well as reliability [1]–[4]. Nevertheless, the demands for extensive quantities of information and widespread interconnection in next-generation wireless networks pose privacy, security, and resource management challenges. Intelligent, automated, and decentralized resource allocation (RA) becomes imperative to address these challenges. next generation generates substantial data from various sources such as social media, machine data, transactions, edge devices, internet activity, sensing, and mobile data, straining existing network resources [3]–[6]. Addressing this necessitates intelligent, adaptable systems at both server and edge levels, necessitating the use of ML. ML enables real-time knowledge extraction from data without explicit programming based on past experiences.
Despite its potential, the next-generation wireless network infrastructure raises security concerns that technologies like blockchain (BC) must resolve. Recognizing these needs, an integrated approach employing ML and BC becomes crucial, equipping communication networks with distinctive traits primarily through BC implemented over ML. Moreover, ML optimizes security, scalability, energy, resource efficiency, privacy, and smart contracts, enabling the creation of safe and intelligent communication networks.
ML-oriented techniques are pivotal in optimizing network performance, even in complex scenarios such as virtual reality (VR), self-driving cars, uncrewed aerial vehicles (UAVs), traffic prediction, image recognition, and online fraud detection. These techniques facilitate real-time application deployment without human intervention, bolstering RA, security, and network trustworthiness [7]. Furthermore, in the era of digital currencies, BC is a hugely intriguing approach that piques the curiosity of both business and academia. A peer-to-peer (P2P) network’s distributed ledger links users. Despite requiring a centralized controller, this decentralized model allows for autonomous and equitable engagement [8]. BC is a flexible block structure that facilitates effective P2P networks, improving governance, resource usage, and information exchange.
As a result, it benefits several industries, including healthcare facilities, security services, and the Internet of Things (IoT), by guaranteeing data validity, integrity, and dynamic access control. Moreover, non-traditional media communication networks can benefit from using the BC [9]–[12]. As a result, these interconnected networks have unique characteristics, including fault tolerance, agility, autonomy, collaboration, and learning [13]–[15]. These characteristics help networks become more cautious concerning security and privacy. To satisfy the growing needs for network densification (ND), extremely low latency, high throughput, positioning accuracy (PA), and EE, researchers attempt to improve the effectiveness of systems at a reduced cost. Smart solutions are essential for making decisions quickly and effectively, conserving energy, and enhancing the performance of wireless communication systems. These solutions include machineand perception-level learning techniques. BC is yet another much-awaited breakthrough technology. BC is a technological framework that combines technologies including chain data structures, point-to-point transfer, decentralized data storage, consensus mechanisms, and algorithms for encryption [16]. The efficiency specifications for 6G networks, including ultrahigh peak rate, extremely low latency, ultra-high reliability, extremely low energy consumption, and seamless communication, expose system security, confidentiality of information, sustainability, scalability, and various other aspects too numerous hazards and obstacles [17], [18]. BC technology is a crucial technological tool for dealing with these difficulties, particularly given the benefits of distributed network design, smart node consensus, and smart contracts. The mutually beneficial use of BC and 6G networks provides secure, highly intelligent, and effective technological assistance for achieving the 6G network goal [19], [20]. The 6G white paper [15] specifically stated that the 6G network requires an endogenous trust network, and BC technology may play a major role in 6G networks to address a range of challenging novel privacy concerns. BC can improve the privacy of 6G networks [21]. Furthermore, BC can offer a solid assurance for 6G networks to create a dispersed, secure, and trustworthy transaction environment. Academic organizations and operators throughout the world are expediting the advancement of crossintegration between novel innovations like BC and artificial intelligence (AI) and 6G networks. In the meantime, 3GPP specifies the network’s data analysis functionality to provide a common interface for developing and applying AI models in wireless networks.
II. PREVIOUS WORKS AND MAJOR CONTRIBUTIONS OF THE PROPOSED WORK
The programmed intelligence information serves as the foundation for every AI model or algorithm. Furthermore, BC is fundamentally a data storage mechanism or “hyper ledger” that includes data intelligence [22]. As a result, both of these closely connected data technologies may be successfully coupled to complement one another and accomplish technological advancement [23]–[25]. BC, as a trustworthy device, can increase the legitimacy, importance, and reliability of AI-generated information. BC advances AI technology by innovating AI cooperation methods and computing paradigms, as well as building an innovative AI environment. AI, with its intelligent and autonomous properties, may facilitate the natural evolution and data sorting of BC via AI algorithm optimization and simulation. Furthermore, AI can successfully avoid BC node forks, handle BC operations more efficiently, and intelligently enhance efficiency. Additionally, the merging of BC and AI can encourage and optimize a variety of applications and services while also providing a dependable, trustworthy, and low-latency smart network infrastructure for contemporary wireless communications. As a result, research into the concurrent implementation of BC and AI over future 6G networks becomes intriguing. Following that, we provide a brief overview of the previous studies on the usage of BC and AI in wireless communication systems. Researchers combined BC and wireless communications to provide safe and trustworthy mobile networks and applications. Several evaluations of BC-supported wireless communications have been issued, with an emphasis on enabling technologies, network architecture, fundamental concepts, research difficulties, and future research targets. These studies may be found in [26]–[31]. Furthermore, various studies have fully investigated the reciprocal relationship between BC and AI [23]–[25] and [32]–[37]. Additionally, the innovative combination of BC and AI for wireless communications has the potential to greatly improve network performance for a variety of services and applications. A large number of scholarly papers [38]–[51] have assessed and summarized the topic of combining BC and AI for wireless communications. To the best of our understanding, none of the previously performed evaluations have delved deeply into this highly debated topic; in particular, few have focused on the simultaneous use of AI and BC for next-generation wireless communications. For instance, [52]’s studies only briefly examined the possibilities of combining BC with machine learning (ML) in wireless communication systems. Comparably [51] provided a brief assessment of reinforcement learning (RL)-powered BCs used in industrial IoT (IIoT) networks. The researchers of [53] evaluated the advantages of implementing BC with ML in an encrypted in-vehicle network. Moreover, large language models (LLMs) such as ChatGPT achieves dramatic progress in recent years. The detailed explanation is also covered in this article. Table 1 compares the study we have suggested to current similar research. Compared to the previously stated works, our study gives a complete analysis and forecast on the present research development of BC and AI for 6G wireless communications. We believe that our investigation will serve as a useful reference for future innovative research in this exciting sector. The primary contributions of this paper are summarised as follows:
· A thorough analysis of a combined BC and AI/ML strategy for communication networks that go beyond 6G.
· A thorough examination of stand-alone ML and BC applications as well as their advantageous incorporation into 6G wireless networks.
· A thorough examination of stand-alone ML and BC applications as well as their advantageous incorporation into 6G wireless networks.
· Conversation about a range of unique ML-integrated scenarios for next-generation wireless networks, such as:
1) ML applications in signal sensing.
2) ML Applications in channel modeling.
3) ML applications in next-generation wireless communications.
4) Federated learning in communication networks.
5) ML for resources and networking optimization.
6) ML applications in anomaly detection for wireless communication networks.
7) ML in network security, resource and network optimization, resource management, classification of network traffic, and routing optimization.
8) ML in SDN, network slicing, network virtualization.
9) ML in unconventional media communications.
10) ML in next-generation IoT.
11) LLM in next-generation wireless networks.
TABLE I
| Research Work | Year | BC for 5G/6G | AI for 5G/6G | BC for AI | AI for BC | BC and AI for 5G/6G | Key Technologies |
|---|---|---|---|---|---|---|---|
| Xing et al. [26] | 2018 | ✓ | ✓ | × | × | × | BC, AI |
| Dinh et al. [27] | 2019 | × | ✓ | × | × | Restricted | BC, IoT |
| Wu et al. [28] | 2019 | × | × | ✓ | × | Restricted | BC, AI |
| Salah et al. [29] | 2019 | × | × | × | ✓ | × | BC, AI, IoT |
| Gill et al. [30] | 2020 | × | × | Restricted | Restricted | Restricted | BC, IoT, SDN, NFV |
| Nguyen et al. [31] | 2020 | ✓ | × | × | Restricted | Restricted | BC, ML |
| Liu et al. [32] | 2020 | ✓ | ✓ | Restricted | Restricted | × | BC, ML |
| Jameel et al. [33] | 2020 | × | ✓ | ✓ | × | Restricted | BC, ML |
| Mohanta et al. [34] | 2020 | ✓ | ✓ | ✓ | ✓ | × | BC, AI, ML, IoT |
| El Azzaoui et al. [35] | 2020 | ✓ | ✓ | ✓ | ✓ | ✓ | BC, ML, DL, RL, FL |
| Pandi et al. [36] | 2020 | ✓ | ✓ | × | × | Restricted | BC, AI |
| Singh et al. [37] | 2020 | ✓ | ✓ | × | × | × | BC, AI, IoT |
| Liu et al. [38] | 2020 | ✓ | ✓ | × | Restricted | Restricted | ML, FL |
| Lin et al. [39] | 2020 | ✓ | × | ✓ | ✓ | × | AI, BC |
| Tahir et al. [40] | 2020 | ✓ | ✓ | Restricted | Restricted | BC, RAN, D2D, SDN | |
| Bhat et al. [41] | 2020 | × | × | Restricted | Restricted | × | IoT, BC, MEC |
| Sun et al. [42] | 2020 | Restricted | Restricted | Restricted | Restricted | Restricted | ML, FL, BC |
| Yue et al. [43] | 2021 | Restricted | Restricted | ✓ | Restricted | Restricted | BC, DApps |
| Sharma et al. [44] | 2021 | × | ✓ | ✓ | ✓ | × | ML, DL, IoT, BC |
| Wang et al. [45] | 2021 | ✓ | ✓ | × | × | × | BC, RAN |
| Rekkas et al. [46] | 2021 | × | × | × | × | × | ML |
| Wang et al. [47] | 2021 | × | × | × | ✓ | ✓ | BC, AI |
| Hussain et al. [48] | 2021 | ✓ | ✓ | ✓ | ✓ | ✓ | BC, AI |
| Tagde et al. [49] | 2021 | Restricted | Restricted | Restricted | Restricted | Restricted | BC, AI, IoT |
| Dhar et al. [50] | 2021 | × | × | × | ✓ | Restricted | BC, RL, IoT |
| Wu et al. [51] | 2021 | Restricted | Restricted | Restricted | Restricted | Restricted | BC, AI, IoT |
| Miglani et al. [52] | 2021 | × | × | ✓ | ✓ | ✓ | BC, DRL, IoT |
| Dibaei et al. [53] | 2022 | ✓ | ✓ | ✓ | ✓ | ✓ | BC, ML, DL, IoT |
| Shafay et al. [54] | 2022 | ✓ | ✓ | ✓ | ✓ | Restricted | BC, DL, ML, FL |
| Yang et al. [55] | 2023 | × | × | × | × | × | BC, AI, Metaverse |
| Our Proposed Work | 2024 | ✓ | ✓ | ✓ | ✓ | ✓ | BC, AI, IoT |
· A thorough examination of stand-alone ML and BC applications as well as their advantageous incorporation into 6G wireless networks.
· Conversation about a range of unique BC-integrated scenarios for next-generation wireless networks, such as:
1) BC-oriented reliability information interfaces for trustworthiness, legitimacy, and authenticity in 6G wireless communication networks.
2) BC-oriented spectrum reframing for next-generation communication networks.
3) BC-oriented rate splitting multiple access.
4) BC-oriented radar-based for next-generation communication networks.
5) BC-enabled energy-efficiency for next-generation communication networks.
6) BC-oriented reconfigurable intelligent surfaces (RIS) for next-generation communication networks.
7) BC-empowered integrated sensing for nextgeneration communication networks.
8) Integrating BC into 6G non-conventional media for next-generation communication networks.
· Have discussions about the incorporation of BC and AI in cutting-edge 6G communication technologies like:
1) Holographic communication.
2) Semantic communication.
3) Molecular communication.
· An overview of discussion on open issues, research challenging issues, and future work are addressed.
Keeping it in mind, given the extensive research landscape, the researchers believe that to the best of their knowledge, no such creative comprehensive study on unified methodology of applications of BC and ML for wireless communication have yet been offered. The remainder of the document is arranged as follows. Section III provides a summary of current ML techniques and their uses. A detailed introduction to BC is provided in Section IV, together with information on its taxonomy, architecture, privileged features, and use in networking and communication technologies. In Section V, the combined use of AI and BC in new, unique next-generation communication technologies molecular communication, holographic communication and semantic communication is covered in depth. The open problems, research obstacles, and solutions are listed in Section VI. The article is finally concluded in Section VII. Fig. 1 illustrates the flow diagram of the proposed survey article.
III. BRIEF INTRODUCTION TO MACHINE LEARNING AND ITS APPLICATIONS
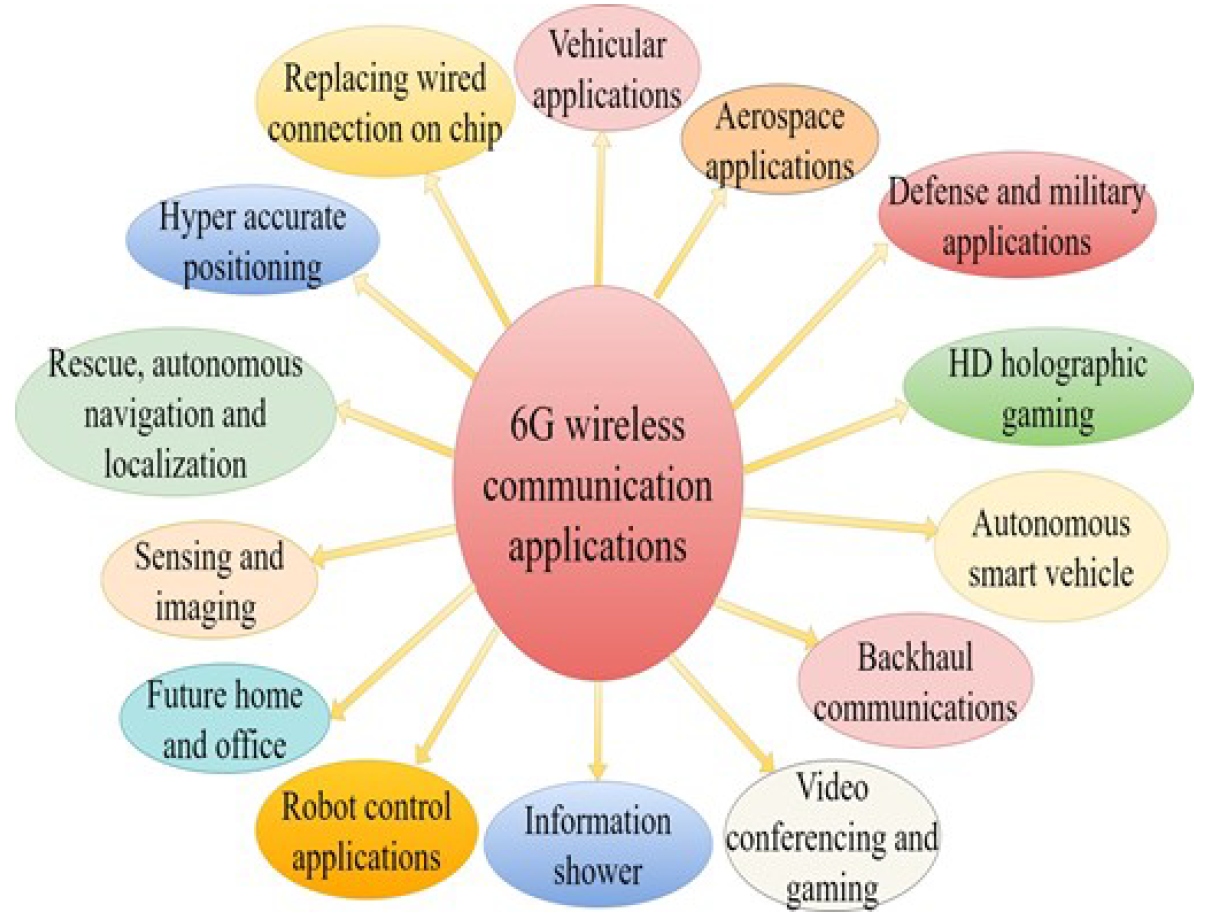
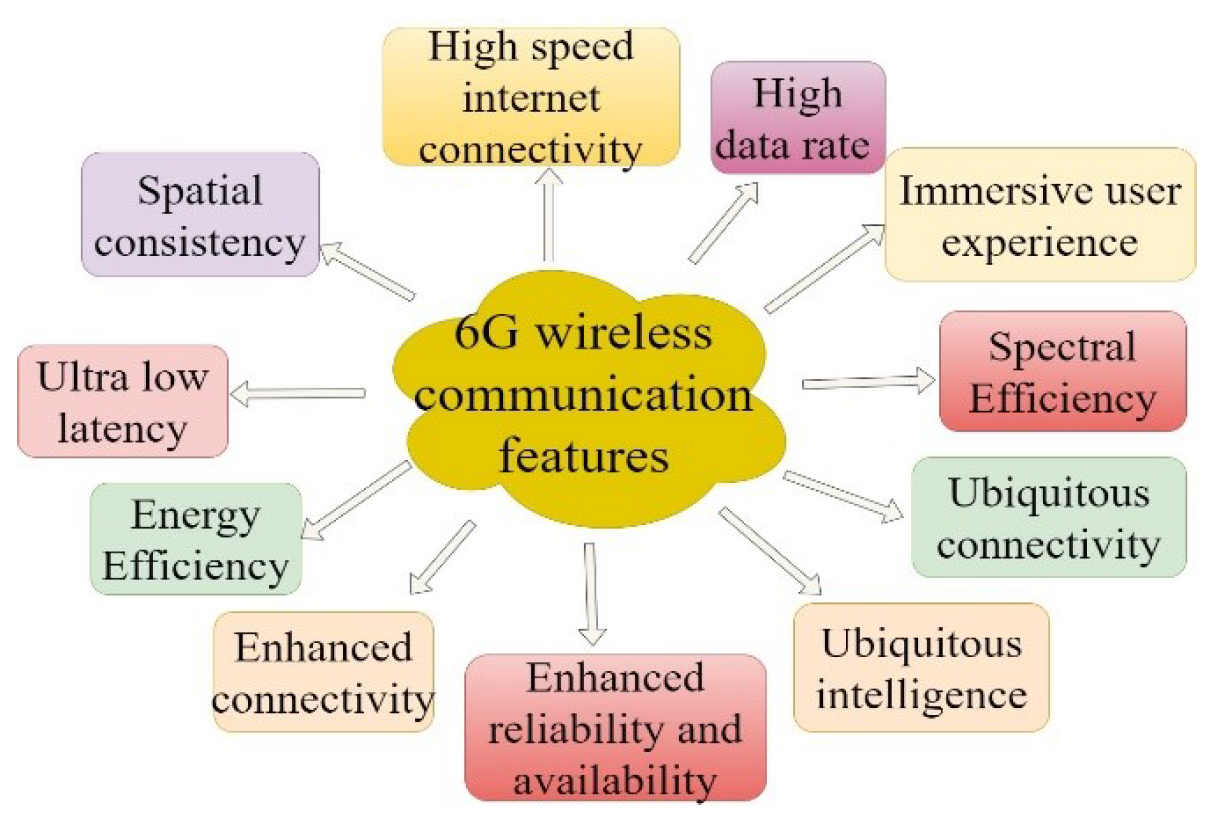
ML, a branch of AI, empowers machines to discover from extensive datasets, covering supervised, unsupervised, and RL. ML algorithms construct models from historical training data during its learning phase, allowing predictions for new tasks based on prior learning. The need for ML in complex and diverse networks arises from their multifaceted nature, posing challenges in meeting communication demands such as high data rate, spectrum efficiency, reliability, network densification, PA, energy efficiency, high throughput, selforganization, and independence. Integrating intelligent techniques is pivotal for effectively addressing these diverse requirements for autonomous system management. Wireless communication has been transformed by incorporating ML approaches, particularly in 5G and next-generation networks. Fig. 2 illustrates the wireless communication applications for 6G wireless communications. Fig. 3 describes the various anticipated features of 6G wireless communications.
A. ML applications in Signal Sensing
Signal processing in wireless communication networks relies heavily on ML techniques. They help to estimate and anticipate crucial system effectiveness characteristics which include signal-to-noise ratio (SNR), bit error rate (BER), and power efficiency (PE). The purpose is to discover the features of incoming signals when they exceed preset criteria [IEEE Std.802.11a] in signal detection. Deep learning (DL) has made substantial advances in signal processing throughout a wide range of fields, including voice support, electronic health, and radar-based applications. DL models built with simulation tools allow for the design of practical smart systems for signal processing [56]. The method includes data management and access obtained via hardware components, computationally generated, or enhanced employing methods like data augmentation.
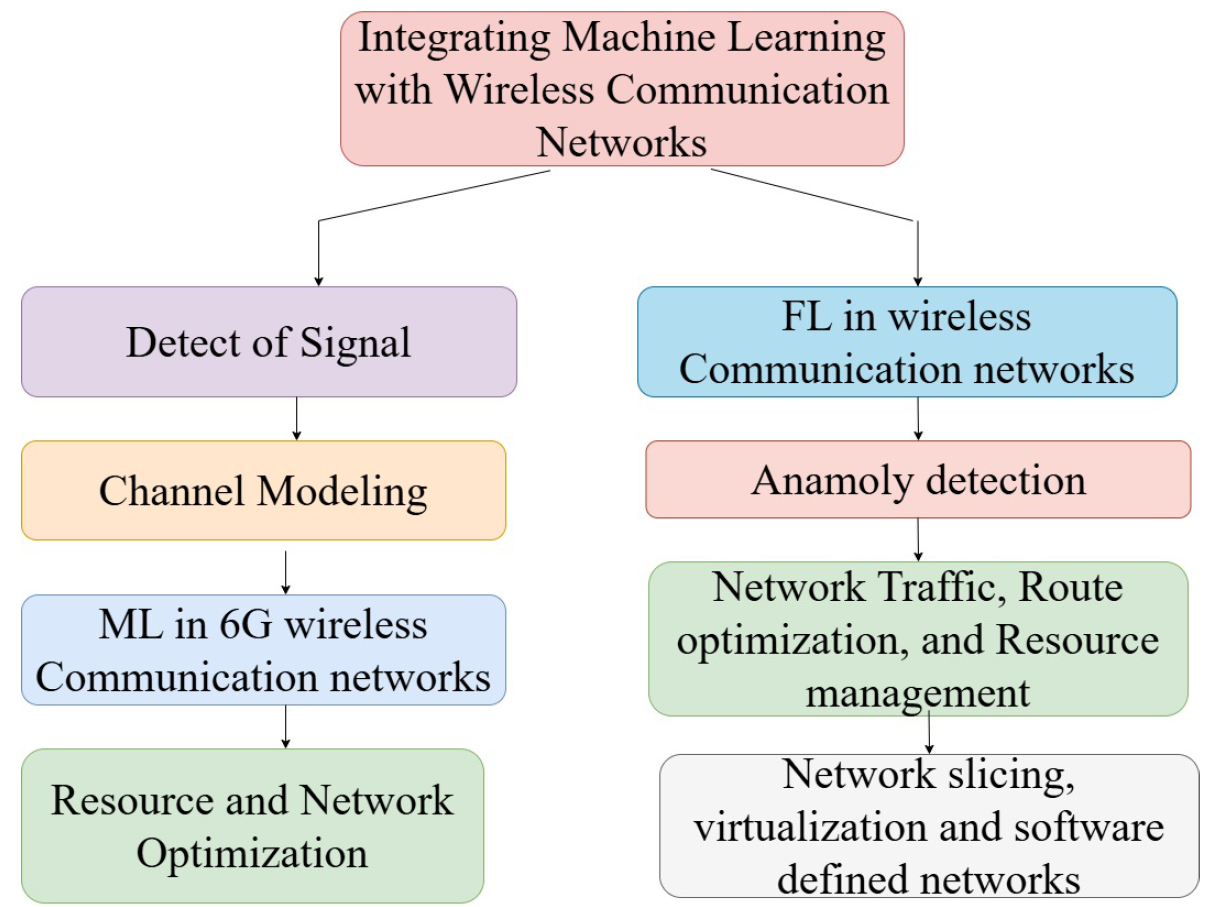
Usually, two main strategies are used in training DL models with ready data. In the initial instance, conversion is required for signals into time-frequency representations and training custom convolutional neural networks (CNN) to extract representations enhancing the visibility of the original signal. Methodologies like constant Q-transform, spectrograms, and continuous wavelet transform are employed. Alternatively, the second approach involves feeding the signal directly into deep neural networks (DNN), such as long short-term memory (LSTM) networks. Minimizing signal dimensionality and variation is crucial for quick pattern learning. One way to achieve this is by directly obtaining characteristics or approaches such as persistent scattering convolutional networks, which automatically gather low variant representations incurring substantial data loss [57], [58]. Fig. 4, shows the ML integration in wireless communication networks.
B. ML Applications in Channel Modeling
The necessity to monitor channel parameters and maximize the utilization of available resources has arisen from an increasing amount of terminal users along with varied service needs in wireless communication networks. Many beamforming antennas will be deployed to combat substantial degradation of path at THz frequencies as the impending next-generation wireless communication age is predicted to include a variety of novel frequency bands. This decade also predicts the creation of large datasets with insightful channel knowledge and full of data attributes. As such, it promotes using the vacant THz frequency spectrum, extensive antenna utilization, and integration of big data analytics. Examining exactly how these developments will affect the next-generation communication environment is essential. The present investigation presents novel distinguishing characteristics including non-stationary in the spatial-temporal frequency range and 3D double-directional angle. It analyses the outcomes of channel modeling, which contain important details regarding channel impulse response. Furthermore, methodologies are applied, including high delay resolution, high path loss, geometryoriented stochastic models, and spherical wavelets [59]. Moreover, there has been much interest in using ML approaches for wireless channel modeling. In particular, channel impulse response estimation, noise filtering, path loss prediction, multipath component estimation, received power estimation, gaussian process regression, received power estimation and channel feature extraction have all been used [60]–[62]. Regression techniques have also been used, including least absolute shrinkage and selection operator. Integrating cuttingedge technology, intensive data analysis, and ML techniques set the stage for the next generation era’s more effective, flexible, and smart wireless communication network. Table II illustrates the comparison of the qualitative features of 4G, 5G, and 6G.
TABLE II
| Attributes | Per Device Peak Data Rate | End-to-End Latency | Maximum Spectral Efficiency | Mobility Support |
|---|---|---|---|---|
| 4G | 1 Gbps | 100 ms | 15 bps/Hz | 350 km/hr |
| 5G | 10 Gbps | 10 ms | 30 bps/Hz | 500 km/hr |
| 6G | 1 Tbps | 1 ms | 100 bps/Hz | 1000 km/hr |
C. ML applications in next-generation Wireless Communications
Due to factors including growing utilisation of smartphones, complex communication situations, deployment of large antenna components, and accessibility to emerging frequency bands, the implementation of ultra-dense small cells and diverse networks have grown ubiquitous in today’s wireless networking environment. As such, there will be an increasing need to investigate and evaluate the large amounts of data that these networks create. The worldwide mobile information has increased eighteen times in the last year, corresponding to a February 2017 white paper from Cisco that highlights the extraordinary expansion of data in 5G and next technologies for communication [63]. The rapid expansion in information supports the use of self-sufficient and sophisticated mobile devices in complex cellular networks. When ML is used in the framework of the 6G network, it improves network performance in handling the massive amount of mobile information load. In the framework of 6G, these ML-driven technologies improve data throughput, power as well as energy efficiency, and latency. In addition, the widespread use of cellphones, large antenna components, and broad frequency band use produces a large volume of mobile traffic data. Large-scale wireless collections of information have specific qualities, such as numerous dimensions, multimodal and personalized elements, and real-time attributes [64]. In real-time environments, multidimensional spatIoTemporal data gathered by many sensors are used to gather user trajectory data. Strong correlations and patterns are evident in these real-time mobile traffic statistics, which incorporate unique statistical properties in a variety of dimensions, such as time and location [65]. Furthermore, the incoming signal in wireless communication consists of closely related multipath signals that experience direct transmission, scattering, reflection, and diffraction. These faded or multipath elements display correlations associated with scatterer distribution, receiver (Rx) and transmitter (Tx) positions, carrier frequency, along with other variables. However, the wireless communication system’s channel state and conditions show regular fluctuations, resulting in a lengthy process to continually execute current models. Recent methods utilize artificial neural networks (ANNs), including radial basis function neural networks and feed-forward neural networks (FNNs), to directly learn from data generated in real-time [3]. These frameworks depends on Artificial Neural Networks (ANNs) have exhibited enhanced accuracy in comparison to conventional random channel modeling techniques. ML applications within wireless communication include a diverse array of tasks, including grouping, categorization, and prediction. The process of acquiring knowledge, educating, and confirming these data sets significantly enhances the network’s effectiveness, precision, and smartness. ML approaches have found extensive application in both outdoor and indoor localization/ positioning tasks. Relevance vector machine (RVM) and support vector machine (SVM) algorithms have proven to be practical solutions for non-stochastic binary and probabilistic categorization, correspondingly [66]–[69]. SVM has also been instrumental in spectrum sensing and antenna selection [70], while different scenarios have seen the deployment of SVM and Naive Bayes (NB) algorithms in antenna selection [71]. Furthermore, a wide range of noteworthy machine learning applications are available, such as cached information, allocation of resources, interference administration, channel estimation, modulation categorization, the scenario designation, user aggregation, route selection according to communication protocols, optimal node implementation, cluster size selection depending on geographic areas, and enhanced cluster dimension categorization.
D. Federated Learning in Communication Networks
Conventional ML methodologies in 5G frequently depend on coordinated gathering of information as well as being processed, which presents issues with sustainability and confidentiality in massive amounts of implementations. In order to overcome these constraints, 6G communication places an emphasis on decentralized and intelligent learning with the goal of connecting intelligence across a variety of devices and things [72]. Developing an approach that prioritizes humans is the main goal, as opposed to approaches that are data-driven solutions, application-centric or machine-centric. Federated learning (FL) appears as an encouraging approach in 6G, specifically designed to uphold confidentiality across public channels. Its significance extends to innovative technologies like augmented reality, holographic interaction, remote area connectivity, self-driving vehicle movement, intelligent railway transport, and industrial automation. The integration of AI in next-generation communications facilitates swift and effective data collection, learning, and transmission, fostering a broad spectrum of innovative services and applications [73]. In comparison to its predecessor, 6G communication is anticipated to offer improved security measures. The integration of FL within the generation removes single-point failures, ensuring robust data-driven ML in large-scale, heterogeneous networks. FL in next-generation empowers decentralized learning at the edge, with private data retained locally on training devices. This edge-level training preserves network security, diverging from central server dependency via the wireless channel. Both academics and industry are paying emphasis to this federated technique for 6G communication [74], [75]. In FL, edge devices cooperate to train a unified model with locally generated data, sending only model updates and thereby maintaining unprocessed data on centralized parametric servers. Nonetheless, obstacles arise from long-range communication costs as well as security concerns, given the multitude of participating parties and diverse elements [76], [77]. By working together, edge devices in FL preserve raw data on centralized customizable infrastructure by employing remotely collected information for developing a shared model and only transferring improvements to the model. Nevertheless, considering the large number of organizations involved and various elements, issues include long-range expenses for communication and safety concerns [76], [77]
E. ML for Resources and Networking Optimization
The implementation of compact, highly populated tiny cells in high-density user locations has prompted the optimization of diverse networks to meet end-to-end quality of service QoS, multimedia traffic demands, and overall efficacy. ML is essential to next-generation communication systems’ resource and network optimization. Intelligent RA, scheduling, and optimization are made possible in very dense and dynamic networks by utilizing ML approaches. Through intensive data analysis and network behavior learning, these algorithms optimize the QoS environment, increase network efficiency, and adaptively distribute resources. Among next-generation wireless communication networks, ML-based techniques help optimize scarce resources, increase network capacity, reduce interference, and guarantee unperturbed connectivity [78]. For instance, RL finds application in RA and scheduling, while techniques such as genetic algorithms, Bayesian optimization, SVM, and particle swarm optimization contribute to RA and optimization. Moreover, ML proves valuable in intelligent beam formation within next-generation wireless networks, guaranteeing uniformity in the tasks assigned. The objective of receive beam forming is to maximize the signal-to-noise ratio (SNR) by choosing the best beam shaper while considering limitations like keeping the signal gain constant.
The next generation wireless communication network performs and is more efficient ultimately thanks to this beam formation optimization. Consider receiving beam formation circumstances in the single input multiple output situation, for example, where any optimization strategies mentioned above can be used. Each of the transmit and receive antennas, the p sent symbol, [TeX:] $$z_i$$ the received symbol on the [TeX:] $$i^{\text {th }}$$ position, and the [TeX:] $$h_i$$-coefficient of fading channel related to antenna i are all taken into account in the sections that follow. Additionally, the system is provided as in [57].
and the respective output signal is
executing the weighted combination of the received signals in this case; still the received signal r is visible as follows.
(3)
[TeX:] $$\bar{w}^T \bar{z}=\left[\begin{array}{llll} w_1 & w_2 & \ldots & w_i \end{array}\right]\left[\begin{array}{c} z_1 \\ z_2 \\ \vdots \\ z_i \end{array}\right].$$To maximize SNR in this network optimization problem, the ideal vector [TeX:] $$\bar{w}$$, must be found. Subject to limitation, the beam can be produced in a certain direction to accomplish beamforming by selecting these ideal weights which, taking into account the first optimization criterion is a convex function, decline with [TeX:] $$\left(\sigma^2\|\bar{w}\|\right)^2$$ signal constraint [TeX:] $$\bar{w}^T \bar{h}=1 .$$ Thus, a convex optimization issue can be defined as the product of the convex objective function with the convex parameter, according to the evaluation shown earlier. Additionally, [TeX:] $$\bar{w}$$ by the use of the Lagrangian multiplier λ deduce [TeX:] $$\bar{w} \text{ in } \bar{w}^*$$ form, that beamformer vector is ideal for whatever
and
where [TeX:] $$\frac{P}{\sigma^2}$$ is the transmit SNR, and [TeX:] $$\|\bar{h}\|^2$$ is the norm of the fading channel vector [71].
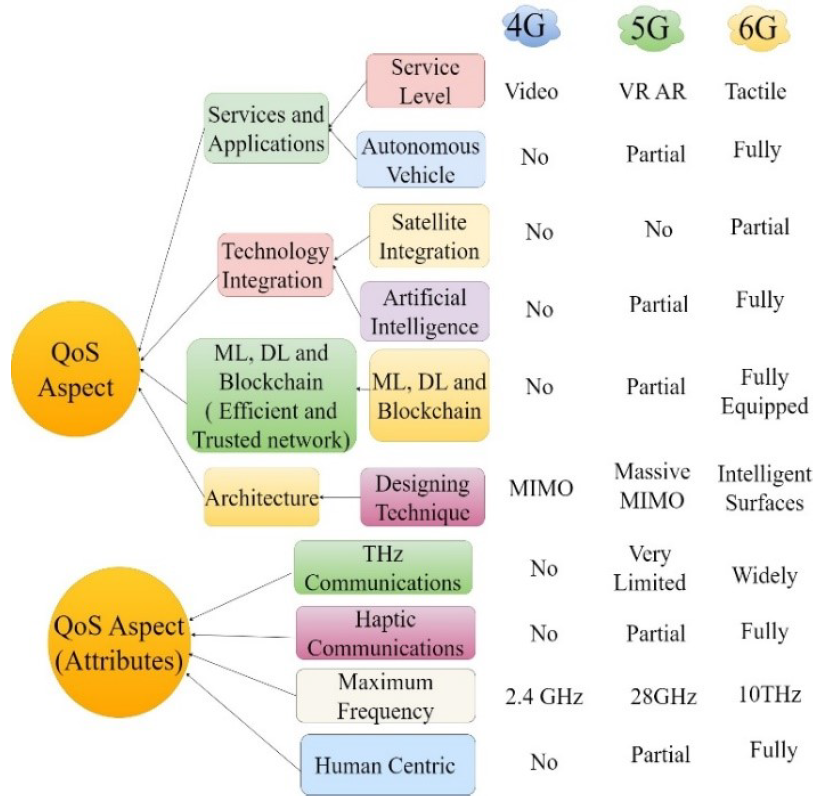
Fig. 5, shows the distinguishable prospective QoS in evolving wireless communication networks a) Overview of QoS in communication technology and b) Overview of QoS in integrated technology. Technology.
Fig. 5.
In this network optimization challenge, the optimum vector must be identified to maximize SNR. By selecting these ideal weights, the beam can be produced in specific directions to accomplish beamforming according to the constraint, which is a convex function. Examine the initial scenario of optimization minimise with
signal constraint
According to the analysis mentioned above, a convex optimization issue may be defined as the combination of the convex objective function with the convex limitation. Applying the formula for the Lagrangian multiplier λ, we can determine [TeX:] $$\bar{w} \text{ in } \bar{w}^*$$ form, that is an optimum beamformer vector with
and
In this instance, [TeX:] $$\frac{P}{\sigma^2}$$ is the transmit SNR, and [TeX:] $$\|\bar{h}\|^2$$ is the standard deviation of the fading channel vector [79].
F. ML Applications in Anomaly Detection for wireless communication networks
Wireless communication networks encompass a wide spectrum, including personal, local, metropolitan, broad region, and secure virtual networks, primarily relying on wireless information links among mobile network nodes [80]. Unfortunately, the shared nature of wireless channels brings up privacy issues and underscores the necessity for robust network security measures [81]. Threats like RF interference, wardriving, bluesnarfing, and encryption assaults are prevalent in these networks, emphasizing the need for intrusion detection systems (IDS) and vigilant network monitoring. anomaly detection (AD) assumes a pivotal function in recognizing network irregularities, employing statistical techniques, streaming algorithms, as well as ML techniques. ML facilitates the differentiation between standard and irregular network behavior, enhancing the efficiency of AD and fortifying network security. Leveraging ML algorithms enables adaptive intrusion detection and real-time classification of network behavior through comprehensive analysis of network data [82], [83]. ML-based AD provides a flexible and efficient method to protect wireless communication networks against harmful actions. In a study by [84], an ensemble learning (EL) algorithm-based AD system was proposed for wireless communication networks. This IDS model incorporates four stages, amalgamated to fortify network security. Notably, extensive utilization of random forests and support vector machines (SVMs) in EL has resulted in heightened network accuracy and reduced false alarms. Additionally, the intricacies of AD by traditional methods were highlighted, underscoring the enhanced capabilities of MLenabled IDS in a study by [85].
G. ML in the Categorization of Network Data, Pathway Optimization, Resource Administration, and Network Protection
This segment explores the applications of categorization of network data, pathway optimization, resource administration, and network protection
1) Categorization of Network Data: Understanding network traffic dynamics, load variations, and demands is pivotal for service providers. Traditional categorization methods, like payload and host-based approaches, come with limitations such as susceptibility to deception, computational intensiveness, and vulnerability to routing asymmetry. ML offers a robust solution for comprehensive traffic analysis, including volume estimation, load balancing prediction, connection analysis, and intensity monitoring. Supervised learning techniques like support vector machines (SVM), kernel methods, and neural networks (NN) are frequently employed. ML enriches efficient data collection, feature extraction, algorithm selection, and model design, resulting in more accurate and enhanced network traffic analysis. By acknowledging these limitations and leveraging ML techniques appropriately, service providers can enhance network resilience, intelligence, and adaptability [86], [87].
2) Pathway Optimization: Route optimization is pivotal in enhancing communication as well as network efficacy. Algorithms for adaptation and finding the shortest route are commonly used, but the high computational complexity of adaptive algorithms restricts their operation in current networks that prefer data-driven algorithms. In comparison, the commonly utilized shortest-path algorithm provides an effective solution with low resource consumption.ML techniques have emerged as powerful tools in tackling optimization issues in network routing, enabling networks to become more autonomous and insightful. Studies have employed bio-inspired algorithms such as ant colony optimization (ACO) and particle swarm optimization to discover ideal routes and prevent link failures [88]. Others have utilized area-based routing algorithms for wireless mesh networks, enhancing speed, duration, and network resources [89]. Regrettably, certain methods that include routing extensions posed vulnerabilities to network failures due to anomalous or defective behavior in authenticated nodes [90]. Within the framework of diverse networks driven by the surge in IoT devices and applications, software-defined networking (SDN) effectively handled traffic bursts [91]. Similarly, enhanced routing strategies incorporated node position, velocity, and cognition, sustaining efficient routing in wireless mesh networks [92]. Utilizing ACO with various protocols in wireless sensor networks improved packet delivery and optimized arrival time, significantly enhancing network performance and ensuring better quality of service (QoS) [93]. These optimization techniques play a crucial role in boosting network efficiency and reliability.
3) Resource Administration: ML empowers networks to attain self-optimization, intelligence, and resilience by innovatively managing resources through dynamic algorithms. In a study [94], the integration of cloud radio access networks (CRANs) with network function virtualization (NFV) and software-defined networking (SDN) created an autonomously optimized network, evaluating SVM, time-delay neural networks, and LSTM for efficiency prediction. A different investigation [95] highlighted the effective handling of resources (RM) in cloud systems to prevent excessive provisioning, introducing optimal schemes like container allocation, task arrangement, and multiple resource coordination. Similarly, in edge computing [96], leveraging unsupervised ML methods such as k-means addressed workload distribution and asset assignment in diverse networks. In 5G C-RAN scenarios, computational analysis RM encountered throughput and latency issues [97]. Issues were resolved using ML approaches and dynamic RM, where the DRMAC-PF framework showed notable improvements. Cloud resource handling, marked by combinatorial challenges, has gained advantages from RLdriven approaches such as Deep RM plus, showcasing enhanced efficiency [98]. Additionally, in resource-demanding IoT and ultra-dense 5G environments, methods like multiaccess edge computing (MEC) and two-time scale deep reinforcement learning reduced offloading delays and maximized resource efficiency [99]. Collectively, these works highlight the pivotal role of ML in refining RM across diverse network conditions.
4) Network Protection: Network protection remains an ongoing issue in network management, as well as ML has arisen as a potent tool for fortifying security through classification, analysis, and detection. The proliferation of devices and applications has made maintaining network security increasingly challenging [100]. ML presents robust abilities in managing large network datasets, facilitating automated acquisition, recognition, discernment, as well as innovation [100]. Security in IoT networks was addressed by proposing a biometric authentication system [101] and a flexible realtime intrusion detection framework utilizing incremental rule acquisition [102]. Network security evaluation using SVM and binary trees was proposed to minimize hazard via structural risk reduction [103]. Extensive data evaluation from the internet framework improved ML-based IDS [104], utilizing hierarchical DL systems for a better understanding of behavior and content features. Unsupervised ML methods like subspace clustering and one-class SVMs were explored for identifying familiar, unfamiliar, and zero-day threats [105]. In wireless sensor networks (WSNs), thorough examination of ML and DL approaches for IDS was conducted [106], proposing a restricted Boltzmann machine-based clustered IDS. Furthermore, a system known as AB-TRAP was proposed for identifying TCP port scanning attacks [107]. An extensive analysis of DL techniques for IDS in WSNs emphasized the importance of ML in boosting network protection [108], covering multiple facets of intrusion detection and defense. These collective studies underscore the pivotal role of ML in fortifying network security and optimizing resource management across diverse network landscapes.
H. ML in Network Slicing, Network Virtualization, and SDN
The evolution of communication networks envisioned in 6G and beyond, aims for pervasive connectivity, ultra-low latency, ultra-high data rates as well as robust support for mobility. These networks are poised to handle dense wireless environments, enable massive machine-type communications (mMTC), and substantially reduce energy consumption. The integration of advanced technologies like NFV, SDN, millimeter-wave, THz communication, network slicing, and cloud edge computing will underpin these capabilities [109], [110].
1) Network Slicing: In 6G and future communication networks, network slicing is an essential technology. Its process is breaking up a physical network into several logical networks, each with its own properties. This situation allows a wide range of frequency applications to be addressed, even ones that need a lot of bandwidth. Specialized network requirements are met by several service classes, as seen in Figs. 4 and 5, which include ultra-reliable low-latency communication (URLLC), enhanced mobile broadband (eMBB), and machine-type communication (mMTC) in 5G and, super URLLC, super eMBB and machine-type communication in 6G. Distributed networks may support a wide range of user needs, such as applications for factory automation and the Internet of Things [110]. With the use of network slicing, E2E slices may be created to meet certain service requirements, and random forest, NB, LR, ANN, and KNN models can all provide reliable answers [111]. In a separate method, the authors in [112] talked about how DL is involved in categorizing packets for various applications across RAN slices while taking evolved packet core (EPC) slicing and application-specific spectrum sharing into consideration. The entire network quality of service is greatly enhanced by the use of network slicing, EPC, and MEC slice. Another investigation uses fog computing to provide cloud capabilities to the IoT edge network. It does this by improving QoS and delay efficiency and classifying priorities using a multi-objective optimisation approach that utilises machine learning [113]. Network slicing is investigated in vehicle-toeverything (V2X) services as a way to satisfy demanding and dynamic needs. In order to ensure developing network efficiency and leveraging virtualization of network servicesy, machine learning techniques are utilised to remotely manage the network and distribute network resources to various slices [114].
2) NFV: NFV is the technique of employing software programmes on commodity hardware devices to carry out network activities. It maximises adaptability and efficiency by enabling the performance of functions like firewalling, load balancing, and routeing on regular infrastructure [115]. NFV seeks to streamline the providing of a broad variety of network services while optimising efficiency and quality of service in the framework of communication networks, including 6G as well as beyond. This creates fresh chances for generating income from cutting-edge services [115]. To facilitate intelligent estimating, anticipating, and automatically configuring models in response to temporal network perturbations, the authors in [116] integrate NFV with ML approaches. In a varied and heterogeneous network environment, NFV makes it easier to construct logically sliced networks customized to meet individual users and applications [116]. Furthermore, the resource allocation issue is addressed by the writers in [117] in compact, diverse IoT networks where inexpensive devices with limited processing capacity are prevalent. The suggested method effectively solves the RA problem by integrating NFV and RL. Optimising data transmission in Internet of Things networks may be achieved by utilising NFV to access network resources and RL algorithms. To satisfy user requirements, the NFV-enabled substrate network facilitates data transfer and service function chaining [117]. Furthermore, NFV is acknowledged as a technology that facilitates efficient and economical operations in the facilities of telecommunications service providers. By using ML techniques, it helps create a zero-touch network and service management framework [118].
3) SDN: SDN is a well-known and crucial approach in the development of communication networks, including 6G and beyond [110]. Controlling network operations in a centralized and intelligent manner is made possible by utilizing software programmes. Network design in heterogeneous networks may be made more sophisticated, evolving, and customized with the use of SDN technology. Thus, a coordinated approach that combines AI and ML greatly improves the network’s economic efficiency, flexibility, security, effective management of resources, route planning, traffic categorization, scheduling, identification of faults, and network security [119]. The estimated accuracy of application-specific machine learning models is investigated by the authors in [120] using the vast and varied data sets gathered via SDN. In a rapidly evolving network environment, appropriate categorization of the gathered data kinds and information is carried out to meet the changing needs of an intelligent communication network. It is advantageous to accommodate new user needs by softwarizing the network using techniques like SDN and NFV [121]. A tremendous amount of data is created every second as a result of the internet’s exponential development in utilization [122]. As a result, cutting-edge methods like cloud computing have surfaced to satisfy these growing needs. SDN provides better QoS, centralized control, lower latency, efficient routeing, and the ability to manage diverse communication networks, all of which help meet the requirement for environmentally friendly networks. SDN improves network efficiency in QoS and autonomous WLANs when paired with MEC and ML [123]. Rapid rises in customer demands lead to a prominence, complexity, and heavy strain of networks. SDN allows for autonomous network administration, traffic forecasting, and centralised management as a clever and proactive strategy [124]. When there are several flows in a network, QoS becomes crucial. In [125], to find the best routes and estimate traffic loads proactively in the future, a QoSaware routeing protocol along with effective rule insertion technique depending on Deep Reinforcement Learning (DRL) are suggested. Moreover, the Internet of Vehicles (IoV), which requires significant processing power, replaces the Internet of Things (IoT) in vehicular networks in [126]. Roadside Unit placement is optimised to maintain security and minimise communication delays, while SDN enhances RM in IoV networks. Additionally, [127] addresses intrusion attacks in communication networks by utilising an ML-based IDS in SDN. The study suggests an anomaly-based network intrusion detection system (IDS) dubbed Neptune that makes use of many ML classifiers and traffic flow characteristics. SDN makes data access throughout the network easier. Furthermore, SDN is helpful in thwarting Distributed Denial of Service (DDoS) attacks; methods like enhanced KNN and DDoS degree aid in detecting and countering such attacks [127]. SDN contributes significantly to improved network intelligence, security, and efficiency overall. Its combination with machine learning techniques allows for proactive management and dynamic network state adaption.
I. ML in Unconventional Media Communication
In contemporary wireless communication, beyond terrestrial networks, an expanding domain of novel media communication exists in underground and underwater environments. ML techniques enhance these ecosystems, imparting sophistication, autonomy, and self-reliance [128]. Despite the potential, these unconventional networks have issues due to their incongruity and harsh environmental conditions, such as limited resources, energy constraints, and Big Marine Data management. ML and DL techniques are instrumental in efficiently managing the enormous data generated in these networks. Nonetheless, given restricted resources and expertise in this field, the advancement of wireless communication for unconventional media has yet to be investigated [129]. Low-energy sensors are utilized in these networks due to their deployment in immense, harsh, an unpredictable channel conditions. Data from these networks holds immense potential for assessing human impact on marine and mainland ecosystems, monitoring pollution, and studying marine life [129]. In this scenario, networks that deploy sensor nodes challenge adequate coverage, leading to their integration with the internet, transforming these networks into IoT ecosystems comprising sensing and communication units. ML and DL techniques, including various NNs [130]. Challenges such as node localization and synchronization arise due to unpredictable channels influenced by various metrics such as temperature fluctuations and marine life interactions. A dense CNN model has been proposed to handle variable underwater acoustic channels, achieving high accuracy in modulation and coding scheme (MCS) level classification [131]. Adaptive modulation and coding techniques enhance transmission parameters based on changing channel conditions in non-conventional networks. Rule-based strategies were initially employed, but limitations led to ML-based approaches improving network efficiency and stability [132]. Predicting physical parameters in underwater environments remains challenging due to sensor node movements. For instance, ML techniques enable efficient system performance in predicting physical parameters like oxygen levels and temperature variations [129]. Balanced routing protocols employing RL-based approaches enhance energy efficiency and reduce latency in non-conventional networks [133]. ML techniques also support underwater wireless optical communication, improving network performance through TL-based frameworks [133]. In summary, non-conventional media communication networks like underwater as well as underground networks face unique obstacles, but ML and DL techniques address these challenges, improving network intelligence and efficiency. ML applications span localization, synchronization, target identification, routing, and optimization, paving the way for advancements in this domain.
J. ML in next-generation IoT
Integrating ML into next-generation-oriented IoT networks is a significant advancement with transformative potential. IoT devices, which are furnished with sensors, computing power, and ML technology, enable information sharing between different industries and sectors, including consumer, industrial, military, and organizational. IoT expands to subterranean and underwater sensor networks in addition to terrestrial networks. The expansive IoT network delivers substantial data from smart devices, numerous sensors, and user demands, posing challenges in effective data management and interpretation [134]. Specific ML models, like the gradient-enhancing decision tree-oriented NN, have enhanced prediction along with explanation performance, enhancing learning ability through hidden layers in NNs. ML techniques find application in diverse fields such as agriculture systems, augmented reality, healthcare monitoring, gaming, and education [135]. For instance, an ML-oriented image compression setup facilitates efficient transmission [135]. ML models use information from traditional pyroelectric infrared sensors to achieve high accuracy in human movement direction recognition. Although learning closer to devices at the edge is preferable, putting learned ML algorithms in the cloud is a more practical solution due to resource constraints. ML approaches optimize spectrum utilization and radio-to-machine communication in cognitive radio and machine-to-machine networks in the IoT. Although installing ML models constrained by resources IoT devices presents a substantial challenge, cloud-based solutions provide a viable way forward by offloading computing loads to robust servers. Combining IoT and ML in cognitive radio networks effectively tackles limited spectrum reliability and optimizes the system’s utility via smart transmission management. ML is also crucial in bolstering IoT network security against cyber threats by detecting anomalies and identifying potential attacks. Moreover, ML approaches improve indoor localization precision and contribute to distributed learning, aiding in analyzing market moods, predicting models, and detecting malware. In conclusion, integrating ML techniques into IoT networks empowers these ecosystems to reach their full potential, enabling intelligent RA, precise geolocation, improved security, and effective data management. ML advances will be crucial in determining the future of connected equipment and services as IoT develops.
K. LLM in next-generation wireless networks
An LLM is a type of AI model specifically designed to understand and generate human-like text. These models are built using deep learning techniques, particularly with neural networks that have a large number of parameters. The integration of LLMs like ChatGPT into 6G wireless networks has the potential to significantly transform how these networks are designed, managed, and utilized. Here’s a detailed look at the impact LLMs could have on 6G:
1) Enhanced Network Management and Optimization:
· Automated Decision-Making: LLMs can assist in automating network management tasks by analyzing vast amounts of real-time data to make decisions on resource allocation, traffic management, and network optimization. They can interpret complex patterns in the network and make predictions about traffic trends, congestion, or potential failures, leading to more efficient and proactive network management.
· Natural Language Interfaces for Operators: LLMs can enable more intuitive interactions between network operators and the network itself. By providing natural language interfaces, network administrators can issue complex commands or queries using plain language, making network management more accessible and reducing the need for highly specialized knowledge.
2) Intelligent Edge Computing:
· Dynamic Content Generation: LLMs at the network edge can generate and customize content in real time, catering to the specific needs of users. This could be particularly valuable in augmented and virtual reality (AR/VR) applications, where LLMs can generate context-aware dialogues, translations, or content modifications.
· Context-Aware Services: With the ability to process and understand context, LLMs can enable contextaware services at the edge of the network. For example, in a smart city environment, an LLM could analyze data from various sensors and provide intelligent, context-aware responses, enhancing user experience and optimizing resource utilization.
3) Personalized and Adaptive Services:
· User-Centric Experiences: LLMs can personalize services for users by understanding their preferences, behaviors, and needs. This personalization could be applied to communication services, content delivery, or even customized network settings, improving user satisfaction and engagement.
· Real-Time Language Translation: In global communications, LLMs can provide real-time translation services, breaking down language barriers and enabling seamless communication across different linguistic communities, which is crucial for applications in international business, tourism, and remote collaboration.
4) Advanced AI-Driven Security:
· Proactive Threat Detection: LLMs can enhance security in 6G networks by analyzing communication patterns and identifying anomalies that may indicate potential security threats. Their ability to understand and process natural language can also help in identifying and mitigating phishing attempts, social engineering attacks, or other security breaches.
· Automated Security Protocols: LLMs can help in creating and managing dynamic, AI-driven security protocols that adapt to emerging threats in real-time, enhancing the overall resilience of 6G networks.
5) Facilitating Human-Machine Interaction:
· Conversational AI for IoT Devices: In 6G networks, IoT devices will be ubiquitous. LLMs can facilitate more natural and intuitive interactions between users and these devices, allowing users to control and communicate with their devices using conversational language.
· Virtual Assistants and Agents: LLMs can power advanced virtual assistants that operate within the 6G network, providing users with personalized support, information, and services based on their specific needs and contexts.
6) Impact on Research and Development:
· Accelerating Innovation: LLMs can assist researchers in analyzing complex scientific literature, generating hypotheses, and even creating code for simulations, thereby accelerating innovation in 6G technologies.
· Collaboration Across Disciplines: By breaking down complex technical language into more understandable terms, LLMs can foster collaboration between different research disciplines, leading to more holistic and integrated solutions for 6G.
7) Challenges and Considerations:
· Data Privacy: The integration of LLMs into 6G networks raises concerns about data privacy, as these models require vast amounts of data to operate effectively. Ensuring that user data is handled securely and ethically will be crucial.
· Energy Consumption: LLMs are computationally intensive, and their deployment in 6G networks may raise concerns about energy consumption. Optimizing the efficiency of these models will be important to align with 6G’s sustainability goals.
· Scalability: The deployment of LLMs at scale within 6G networks will require robust infrastructure and efficient distribution of computing resources to ensure that the models operate effectively without causing network bottlenecks.
In conclusion, LLMs like ChatGPT have the potential to revolutionize 6G wireless networks by enabling more intelligent, personalized, and secure services. However, careful consideration of the associated challenges, such as data privacy, energy consumption, and scalability, will be crucial to fully realizing their potential in the next generation of wireless communication.
IV. OVERVIEW OF BLOCKCHAIN
Originally devised for cryptocurrencies, BC has evolved into a pivotal element in wireless networks, fostering secure connections among anonymous entities. It serves as a distributed collection of data ensuring secure and unchangeable record-keeping through cryptographic methods. Comprised of interconnected blocks forming an ever-expanding chain of records, BC presents a promising avenue for ensuring secure and dependable data sharing within wireless networks [136]. This segment offers an in-depth exploration of the foundational aspects of BC, its indispensability, significance, attributes, diversity, and architectural underpinnings. We delve into its application in wireless communication systems and unconventional media networks.
A. Embracing the Unique Attributes of BC
As the IoT expands rapidly, wireless networks encounter heightened complexity and widespread usage, thus encountering escalated security risks. This underscores the pressing need to leverage the multifaceted advantages of BC. With the exponential rise in internet use and data generation, BC regulation becomes imperative to govern digital commerce, safeguard confidential individual information, and ensure robust network security and privacy. Additionally, BC’s applicability extends to underground, air, and underwater networks, alongside securing medical data sharing, IoT, network logistics, government services, and supply chain management. These applications drive the exploration of BC in wireless networks, spurred by its groundbreaking role in the realm of cryptocurrencies. BC operates as a network of linked blocks subject to particular regulations. Every block in the BC keeps the hash that was produced by the block before it, creating an unchangeable record of all digital events and transactions. Through its decentralized framework, BC adeptly manages the digital landscape via centralized control or human intervention. It capitalizes on attributes like anonymity, pseudonymity, decentralization, transparency, autonomy, immutability, and audibility to orchestrate a robust digital ecosystem [137]. In the domain of next-generation wireless communication networks, the fusion of BC with ML holds substantial significance. BC serves as a reservoir of crucial insights within wireless networks, offering details such as optimal routing protocols, node identities, node power status, existing spectrum information, network optimization metrics, and profiles of potential fraudulent nodes. Particularly in intricate and varied communication networks, the dynamic nature of channel conditions often poses challenges in assessing network performance metrics. Consequently, smart contracts emerge as intelligent solutions, operating as automated computer programs that execute specific agreement terms, thereby contributing significantly to the efficient management of networks. The synergy of BC, ML, and the deployment of smart contracts sets the stage for the establishment of secure, dependable, and enhanced networks for wireless communication.
B. Assortment and Framework of BC
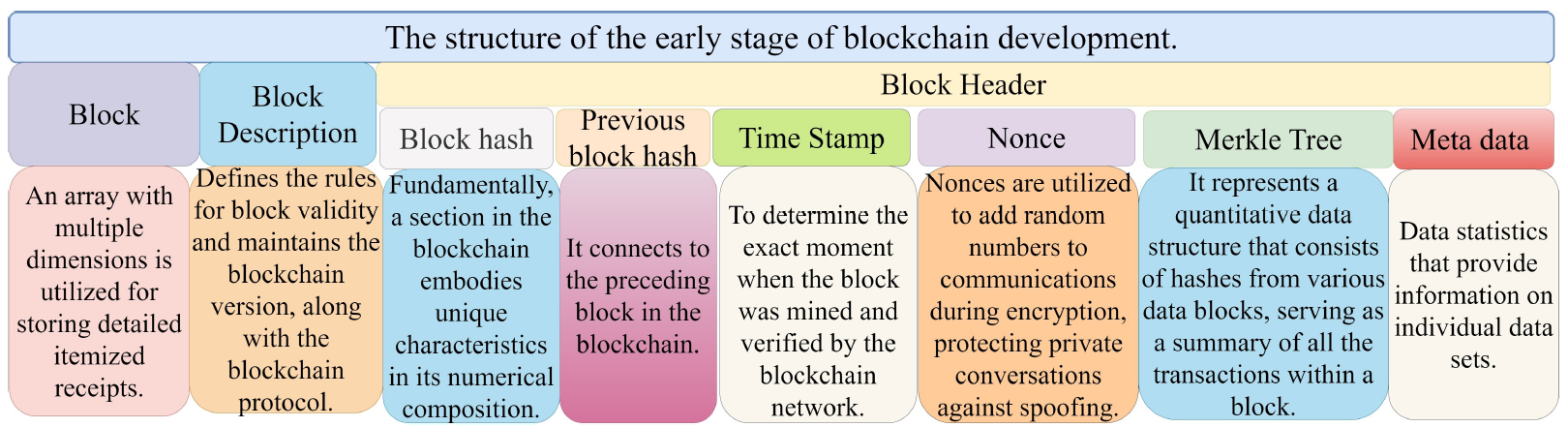
The framework of BC operates within a decentralized network where multiple nodes maintain duplicates of the complete collection of data, removing the necessity in favor of a central power. This strategy amplifies reliability and privacy. The adaptability of BC is evidenced by its diverse services, spanning supply chain management, smart contracts, digital identity management, and cryptocurrencies [138]. Furthermore, the control and access layer of BC employs decentralized ledger construction aligned with the network’s demands. It adheres to predefined governance rules overseeing operational and administrative duties. Through the integration of privacy, activity, authorization management, and network and node-level access controls, these laws provide users with the ability to utilize BC resources and services. Fig. 6 details the visualization depicting the progressive architecture of BC. Varying permission levels determine data read or write access, necessitating a well-designed system to ensure seamless operations, whether in public, private, or generalized network environments, for instance, Ethereum.
1) Structure of BC: BC stands as an immutable network facilitating secure digital exchanges and maintaining an unalterable log of internet traffic made up of linked blocks. These blocks, once formed, cannot be modified, ensuring perpetual verification. Ledger record verification usually involves a peerto- peer (P2P) network of users reaching consensus on block alterations. The BC architecture incorporates network protocols, decentralization, cryptography, decentralized networks, tokenization, blocks, security, privacy, consensus mechanisms, and smart contracts as detailed in this section. We examine important elements of BC, which include networks, frameworks, consensus techniques, and blocks. A block consists of a block header along with a block body that keeps transaction data. The block header includes elements like timestamp, nonce, Merkle tree root, block validation criteria, and a hash of the parent block. The amount of transactions and the block’s size influence its capacity. There are two different kinds of nodes in the BC network: full and light nodes, each with unique capabilities [139]. Novel applications of BC have been investigated, such as integrating it with current cloud technologies to improve cloud data center productivity, performance, security, and safety [140]. Applications for BC can be found in a variety of fields, such as confirming identity and following the origin of an object via a chain of possession. A hierarchical design for decentralized application development is presented by the authors in [141]. These contracts, which have been extensively researched in the literature, serve to include computer programs used in applications relevant to BC including Hyperledger and Ethereum. Having records kept within the BC, stakeholders uphold certain agreements about acts or exchanges taking place across a BC P2P network. The order in which transactions occur establishes the status of contracts.
2) Consensus Mechanisms: Consensus procedures are used by a BC, a decentralized public ledger that is jointly maintained by the network, to guarantee a precise as well as accessible occurrence history. PoW-based consensus has limitations, including increased energy consumption, decreased transaction frequency, and network delay, even if it can handle a large number of unreliable entities. The particular needs and uses of the BC framework will determine which consensus technique is best. Innovations like proof of elapsed time (PoET) and proof of stake (PoS) address energy efficiency concerns, reducing the reliance on computationally intensive mining. Additionally, block-being-approved techniques that utilize Byzantine fault tolerance (BFT) unanimity have been investigated by academics.
3) BC-oriented Reliability Information Interfaces for Trustworthiness, Legitimacy, and Authenticity in Next Generation Wireless Communication Networks: BC has become apparent as a feasible resolution. for addressing diverse challenges and security vulnerabilities in communication networks, offering efficient resource sharing, trustworthiness, safe authorizations, and enhanced privacy features. In next-generation wireless communication networks, heightened due to network heterogeneity and a variety of demands from users, there is wireless congested and accessibility abundance. create challenges in establishing secure interactions and verifying authenticity and integrity among data owners [142]. Recent research endeavors have employed BC to foster dependence on each other among equipment, establishing a dependable route for very safe data exchanges [143]. Within BC-oriented next-generation networks, multiple BC nodes play critical roles and must operate reliably to maintain QoS. Assigning trust values to each node based on historical actions and authorization helps in determining their identification and reputation. To provide a safe, autonomous, self-sufficient, and decentralized network, edge computing is introduced into next-generation wireless communication networks. Cluster-based intellectual assessments and consensus processes guarantee the legitimacy and accuracy of the data. A BC-oriented trustworthiness strategy for edge computing data governance utilizes affirmation methods aBC has become apparent as a feasible resolution. for addressing diverse challenges and security vulnerabilities in communication networks, offering efficient resource sharing, trustworthiness, safe authorizations, and enhanced privacy features. In nextgeneration wireless communication networks, heightened due to network heterogeneity and a variety of demands from users, there is wireless congested and accessibility abundance. create challenges in establishing secure interactions and verifying authenticity and integrity among data owners [142]. Recent research endeavors have employed BC to foster dependence on each other among equipment, establishing a dependable route for very safe data exchanges [143]. Within BC-oriented nextgeneration networks, multiple BC nodes play critical roles and must operate reliably to maintain QoS. Assigning trust values to each node based on historical actions and authorization helps in determining their identification and reputation. To provide a safe, autonomous, self-sufficient, and decentralized network, edge computing is introduced into next-generation wireless communication networks. Cluster-based intellectual assessments and consensus processes guarantee the legitimacy and accuracy of the data. A BC-oriented trustworthiness strategy for edge computing data governance utilizes affirmation methods and user-defined dedicated data encryption. Additionally, decentralized trust-based management systems proposed in [144] employ BC for green communication and network establishment, assessing traffic communication trustworthiness through a Bayesian interference framework. Fig. 6 details the architecture of BC specifically in the communication layer. Moreover, a proof-of-evidence (PoE) agreement paradigm is introduced for vehicular communication, leveraging passing motorists and vehicles to authenticate congestion information recorded by roadside devices [145]–[147] and user-defined dedicated data encryption.
4) BC-oriented Spectrum Reframing in 6G Wireless Communication Networks: In contemporary wireless communication, repurposing existing bands like transitioning from lower to higher band spectrums can efficiently cater to diverse services. For instance, a spectrum reframing (SR) technique based on the GSMA can elevate lower band technologies, transforming GSM from 2G to more advanced systems such as Universal Mobile Telecommunications System (3G), Long- Term Evolution (4G), mMIMO, beamforming, mm-wave in 5G, and emerging technologies like visible light communication (VLC), THz spectrum, RIS, AI, and data-centric automated processing in 6G. Table III: Implementing such SR techniques in 6G wireless networks promises augmented network capacity and efficiency within the existing resources, crucial in densely populated user environments and various service scenarios. Spectrum reframing serves as a radio resource management technique, enabling different generations of cellular networks within the same spectrum band. Notably, prior works, such as the underlay OFDM-based SR model proposed in [148], illustrate efforts to share spectra in code division multiple access systems. However, these methods, while effective, exhibit static behaviors that impede network scalability. Efforts like the dynamic broadband SR model proposed in [149] enhance network efficiency by leveraging OFDMA systems. These concepts are adaptable to 6G networks, exploiting untapped spectrum resources to address the diverse needs of an extensive user base. However, security remains a concern due to the wide-ranging demands and infrastructure complexities inherent in wireless networks, necessitating secure technologies like BC.SR confronts significant challenges: centralized resource allocation, security vulnerabilities, high administrative costs, intermediary spectrum purchases, cyber threats, and sluggish spectrum-sharing procedures. Leveraging BC characteristics within 6G spectrum reframing enhances spectrum usage visibility and audibility for terminal users, ensuring network transparency. BC, with its trustless, decentralized resource trading platform, ensures an efficient and secure network, vital for maximizing available resources in SR techniques effectively.
V. DISCUSSION ON OPEN ISSUES, RESEARCH CHALLENGING ISSUES, AND FUTURE WORK
In the previous sections, we discussed future initiatives in BC, and AI integration for 6G wireless communications is a popular area of research right now. We looked into the potential applications of mixing BC with AI in the earlier parts. Furthermore, we talked a lot about how BC and AI may be used for wireless communications, including smart IoT applications and secure services. Though there are still many unanswered problems and difficulties, research on combining BC technology with AI for wireless communications is only getting started. In this part, we summarize the potential open concerns and research obstacles for incorporating BC and AI in 6G wireless communications, based on in-depth study works in current literature. The intention is to offer useful sources of inspiration and information n for the next studies on innovation. We also discuss future research possibilities that may be pursued.
A. Towards BC
The investigation and execution of BC technology have started to increase rapidly in the last few years. BC is thought to be the primary technology that will transform the informational Internet of today into the value-based Internet. BC technology offers a lot of potential for 6G networks, however, there are now several obstacles preventing its broad use in these networks. Scalability is the main obstacle preventing BC technology from being widely used in 6G networks as transaction volume rises dramatically. Huge transactions are processed by the Visa system every second, but the typical processing speed of the Ethereum and Bitcoin systems is between 7 and 20 transactions per second. A significant amount of extra storage space is also needed for the BC’s multi-copy capability, which raises storage expenses. Largescale apps will have a hard time being supported due to the constrained space utilization that will follow. Using methods like sidechains, lightning networks, sharding, pruning, and directed acyclic graphs, several academics have improved the scalability of BCs. These approaches do still have certain drawbacks, though, such as which transactions to cut and how to split the tiles evenly. Furthermore, the BC sector uses a lot of electricity. To give an example, the BC architecture that uses the PoW consensus method depends on the processing power that each BC node contributes. Nevertheless, only a portion of the computational capacity has been rewarded, and the remainder is squandering a lot of resources by performing ineffective tasks. The issue of excessive energy consumption has an impact on BC’s adoption and popularity of 6G. The primary challenge that the BC has encountered thus far is security attacks, including the 51% attack on Bitcoin and the botnet threat. The advancement of mathematics, cryptography, and computer technology will make the BC’s asymmetric encryption process increasingly fragile. The further integration of BC technology into 6G networks is also seriously threatened by security concerns. The openness and transparency of the data transactions recorded on the BC are advantageous for data exchange and verification, but they do not help protect user privacy. Privacy leakage is becoming another major concern as personal data is being kept in 6G networks enabled by BC technology.
B. Towards AI
AI, particularly deep learning, has made significant strides in computer vision, natural language processing, speech recognition, and other areas in recent years. To create an intelligent communication system, realize the genuine interconnectedness of everything, and satisfy people’s constantly shifting needs for data transfer speeds, the researchers want to apply AI to every level of the 6G system. Nonetheless, there are still a lot of difficulties and unresolved problems with setting up and running sophisticated intelligent communication systems. AI, particularly deep learning, has made significant strides in computer vision, natural language processing, speech recognition, and other areas in recent years. Another unsolved issue in heterogeneous networks is combining data from several sources to train models. Users want low latency and fast throughput, for instance, even at the expense of security in video streaming apps. Even so, consumers of payment software need robust security, even if it means sacrificing speed. Developing a based-on-action, cross-layer AI protocol for diverse applications is crucial in meeting diverse service requirements and maintaining network resource equilibrium in 6G networks. Especially in this fast-paced age of AI development, concerns about privacy and data security are becoming more and more important. By enabling AI features, 6G networks achieve linked intelligence. However, because of their centralized network design, they are susceptible to hacker assaults. Furthermore, a 6G network must gather a lot of user data from billions of devices to train it. AI has the potential to cause user data privacy breaches due to the training data’s high level of personal information. AI-enabled 6G network designs may be designed using distributed technologies to become decentralized, reliable security systems. Because distributed technology processes data locally rather than transmitting it all to the cloud computing center, it can somewhat mitigate the issue of privacy leakage. However, communication is necessary to share the information that each party perceives and to update each party’s knowledge bases jointly. This increases the possibility of local data privacy leaks. It is still urgently necessary to figure out how to create an effective system for coordinating among communication participants without allowing any private information to leak.
C. Towards BC and AI-Assisted Wireless Communications
BC and AI integration opens up novel opportunities for 6G networks, but it also presents several unresolved problems and research obstacles. Consider the inherent conflict that exists between BC technology and AI, the processing of massive volumes of data, and the cooperative optimization of several systems and indications. Furthermore, widespread use of wireless communication networks is still required to confirm the viability and efficacy of BC- and AI-assisted wireless communications. The use of AI and BC together has certain drawbacks. For instance, smart contract execution outcomes in BCs are frequently deterministic. However, the majority of the time, the outcomes of AI algorithms’ execution are unexpected, random, and uncertain. The incompatibility of BC technology and AI presents significant obstacles for BC-integrated AI systems seeking to maximize 6G network execution choices. To resolve the dispute between the security of smart contracts and the unpredictability of AI algorithms, more research will be needed in the future. The novel strategy can create consensus procedures for every BC node that participates as well as manage approximations for smart contracts. The new solution aims to provide judgment outcomes under the 6G network that have elevated precision, high accuracy, and specific confidence. The processing of massive volumes of data in BC- and AI-assisted wireless communication systems is an enormous issue given the fast rise of information in 6G networks. BC is usually employed to safely gather and store vast volumes of data, which AI then processes for model training. For AI training, the enormous unlabeled and unclassified datasets are insurmountable. However, there is a chance that the BC will cause bottlenecks when it comes to storing this vast amount of dispersed information. For instance, the information stored on the BC is transparent and available to anyone. While the BC-based storage approach helps with data verification and distribution, it is not good for protecting data privacy. Moreover, the majority of publications in relevant literature types now in publication frequently only optimize one performance metric in a single wireless communication system. Ignored is the cooperative optimization of many wireless communication systems’ performance indices. But when BC and AI technologies develop and are thoroughly studied in the future, it will be possible to integrate the many solutions suggested to improve the functionality of various wireless communication networks. Thus, it is possible to accomplish the aim of co-optimizing numerous system performances. Based on the material that is currently available, BC- and AI-assisted wireless communications are still in their infancy. Numerous projects use BC technology to deliver a secure wireless communication infrastructure and offer AI algorithms for wireless communications networks’ prediction, optimization, identification, detection, including decision-making. Very few efforts have truly incorporated AI and BC with wireless communications. It will take a lot of time and uncertainty to fully integrate and execute BC and AI technologies for 6G networks, regardless of how we measure it in terms of the current technical metrics of BCs or the practical deployment of AI and 6G networks. It’s also challenging to evaluate the possible effects of combining BC technology with AI for 6G networks. As such, we need to approach the integration of BC and AI for 6G networks with reason and realistic execution in mind, even as we aggressively investigate this avenue. We will persist in using a natural amalgamation along with an adaptable and inventive methodology to effectively actualize the implementation and investigation of BC and AI integration in 6G wireless communications.
D. BC-oriented Rate Splitting Multiple Access for next-generation wireless communication networks
“Rate splitting multiple access (RSMA) presents a promising avenue for 6G networks, offering efficient resource utilization, reduced interference, and heightened system performance [150]. Employing RSMA within 6G wireless communication networks augments system capacity and overall performance by enabling users to partition their transmission rate into common and private segments. RSMA improves network capacity and spectral efficiency by utilizing interference and allowing for synchronous channel access. By combining these segments, users can experience heightened data rates without compromising resource allocation, thereby accommodating more users within the network’s constraints. Despite its efficacy, RSMA poses security challenges, prompting the exploration of BC-enabled RSMA techniques. Integrating BC fortifies the network’s security and transparency, harnessing BC’s strengths to fortify the system against vulnerabilities. BC permits scalability in RSMA methods inside 6G networks, giving a decentralized framework for the adaptive distribution of resources among users.With BC, the network autonomously manages resource allocation across nodes, accommodating diverse users and devices. Automated bandwidth allocation facilitated by BC promotes network scalability and accommodates an expanding user base. The decentralized nature of BC streamlines resource distribution, minimizing bottlenecks and enhancing overall network scalability and performance.
E. BC-oriented Energy-Efficiency for next generation wireless communication networks
In the realm of 6G networks, significant energy demands loom large, potentially contributing to heightened emissions of carbon and consequences for the environment. However, envisioning a BC-enabled 6G network introduces the prospect of leveraging a distributed energy system reliant on renewable sources like solar or wind power. This strategic approach holds promise in curbing the environmental footprint of the network while concurrently slashing energy consumption expenses. Additionally, the integration of BC within a 6G setup could establish a fortified and decentralized communication platform, fortifying privacy, enhancing security measures, and minimizing network vulnerability to cyber-attacks [151]. The transformative potential of a BC oriented, energy-efficient 6G wireless communication infrastructure is undeniable, offering a Reliable, decentralized, and renewable communication framework. Demonstrating the versatility of BC within a diversified 6G network, several energy-efficient approaches can be implemented [152]. The application of BC within the realm of 6G wireless communication systems emerges as a transformative force, optimizing energy usage, fostering energy trading, incentivizing efficiency, streamlining network operations, and upholding data integrity [153].
F. BC-oriented Radar based next generation wireless communication networks
Radar and wireless communication are integral components of radio frequency technologies, with radar used for target detection and communication facilitating information exchange among devices. Historically, these technologies have evolved independently, operating in distinct frequency bands and serving different purposes [170]. However, the escalating spectrum constraints due to the proliferation of wireless devices amplified data traffic, and the demand for enhanced radar capabilities in intricate electromagnetic environments underscore the necessity of integrating these technologies. This integration promises heightened efficiency and effectiveness, fostering swift data fusion and optimizing resource utilization [171]. Undeniable, offering a secure, decentralized, and sustainable communication framework reliant on secure and reliable communication. While the prospects are exciting, numerous technical and practical hurdles need addressing problems. Nonetheless, this realm of research and development holds promise for substantial advancements in wireless communication and network security. BC- radar communications integration potentially enables networks to securely store activity logs and critical data in a transparent, traceable, and impervious manner, safeguarding against unauthorized access or manipulation. For instance, BC-based distributed ledger technology could establish a secure, decentralized record of network events, offering insights to monitor, analyze, identify security threats, and optimize network performance.
G. BC-oriented RIS for next-generation wireless communication networks
The integration of BC Technology with 6G RIS communication introduces the transformative potential of communication paradigms. RIS, a significant component in the envisaged 6G wireless network, consists of passive elements altering electromagnetic waves (EMW), effectively enhancing signal-tonoise ratio and refining wireless communication quality [172]. Yet, several security concerns loom over RIS, encompassing unauthorized access, privacy issues, secure configuration, and malware vulnerabilities, demanding a robust solution prompting the integration of BC. In [127], a proposal for 6GRIS in D2D communication emphasizes passive beamforming and power control to enhance Energy Efficiency (EE). However, effective network operation demands frequent and decentralized RIS configuration updates, fueling the rationale for integrating BC with 6G-RIS. A key application of BCoriented next-generation RIS resides within the IoT sphere. Employing BC in RIS technology bolsters signal quality and IoT device coverage while upholding transparent transactions and securing exchanged data. Similarly, in the domain of smart cities, BC-integrated RIS technology facilitates WSN, ensuring network integrity while covering expansive areas. The amalgamation of BC and RIS promises novel enhancements to wireless communication, underlining a more secure, decentralized network architecture [128].
H. BC-empowered Integrated Sensing for next-generation wireless communication networks
The fusion of BC with the next generation forms a robust backbone, enabling seamless communication and information sharing among devices and users. Allowing devices to gather environmental data and forward it to the BC for evaluation. An RA scheme was proposed in [137] but faced challenges in managing multiple concurrent requests while ensuring data integrity. In [138], a joint communication and sensing framework (JCAS) highlighted security concerns due to extensive signal interaction with the environment, increasing eavesdropping risks. Addressing the combination of digital/analog massive MIMO low-earth orbit satellite equipment, [173] introduced a beam squint-aware ISAC technique. However, dynamic channel conditions posed challenges by causing information fluctuations. FL was explored in [174], involving edge devices transmitting signals to sense objects collaboratively, emphasizing stringent security measures. Further exploration in [129] and [175] delved into ISAC’s utilization in vehicular communication, stressing decentralized parameter updates for roadside units using BC to ensure network smoothness and prevent accidents. The resulting BC-fueled next-generation ISAC network amalgamates BC, next-generation, and IST, catering to several applications in fields like health care, transportation, and smart cities [147]. These networks facilitate real-time monitoring, offering efficiency enhancements and safety improvements [148]. The BC element fortifies the ISAC network, providing a secure and decentralized platform for data storage, processing, and verification. This ensures data integrity, and privacy, and safeguards against unauthorized entry. Additionally, BC’s distributed administration ensures transparency and impartiality across the network, which is ideal for applications demanding fairness and openness. For instance, it could remotely monitor patient health or regulate traffic flow in real-time. In summary, a BC-boosted nextgeneration ISAC network is poised to outperform existing architectures, delivering substantial advantages in efficiency, security, and reliability.
I. Integrating BC into Unconventional Media Communication for next generation wireless communication networks
The rapid growth of smart cities has been propelled by the IoT’s influence across human life domains, including underwater domains. A substantial part of the Earth’s surface is underwater, much of which remains unexplored. This backdrop has led to the emergence of the Internet of underwater things (IoUT), a system of linked, autonomous underwater equipment used for defense, minimizing disaster risks, underwater research, and environmental surveillance. However, ensuring security and validating entities in autonomous underwater device exchanges pose challenges due to concerns about security and rogue nodes.
Traditionally, merged privacy and identity protocols rely on trustworthy third parties, resulting in increased computing costs and energy consumption, in particular for submerged communications. BC offers an efficient solution, proving the promising for enhancing next-generation wireless communication networks [176]. To tackle In consideration of this, the researchers suggested an efficient in terms of energy cooperative analyzing technique. using BC, leveraging BC cryptography to ensure confidentiality [175]. Additionally, in [150], the discussion centered on integrating off-shore wireless communication, satellite links, and non-traditional media into the nextgeneration network. It is anticipated that this integration will create extensive connectedness in aquatic environments, aided by AI to facilitate network service evolution. The challenges of fluctuating channel scenarios, sporadically embedded nodes in deep water, and data generated by various applications like environmental monitoring and defense highlight the need for effective data management strategies [177]. Tables III, IV, and V demonstrate the comparison of the recent existing works on the integration of both BC and AI and describe its perspective and description.
TABLE III
| Author and Publication Year | Perspective | Description |
|---|---|---|
| Saida Maaroufi [154], 2021 | Insightful depiction | BC-oriented ML-based congestion management system for the future generation of vehicle networks. |
| Ensuing Detention | BCOOL, a revolutionary BC congestion control system for automotive networks, is introduced in this paper. To control message and vehicle trustworthiness, BCOOL uses a dynamic hybrid fogbased decentralized trust contract technique to bridge the gap in reliable BC congestion forecasts. | |
| Adverse consequences and assessments | To enhance performance for real-world applications, future BCOOL designs could consider loosening a few of the technique’s limitations. | |
| Final conclusion | According to simulation studies, under a severe data congestion technique, BCOOL outperforms other comparable approaches by 85% and 100% with regard to reliability and efficiency improvements. | |
| Alia Asheralieva [155], 2021 | Insightful depiction | MEC using Bayesian RL with BC. |
| Ensuing Detention | The researchers propose a game-theoretic approach for behavior miners across both public and consortium BC environments by using Bayesian RL and DL in MEC. | |
| Adverse consequences and assessments | Organizations are supposed to be aware of one another’s strategies in the game-theoretic framework and be able to construct a payoff matrix in order to assess various alternatives. | |
| Final conclusion | A unique RL and DL framework has been provided by these researchers to describe the interactions between miners in a BC and MEC. Stochastic games with insufficient data are taken into consideration by the model. | |
| Dhaou Said [156], 2021 | Insightful depiction | ML and BC are used to create a decentralized power marketplace for the connected vehicle. |
| Ensuing Detention | To increase road safety and lessen traffic congestion, the researchers created a decentralized intelligent contract framework for connected electric cars (CEVs). The technology allows CEVs to purchase and sell power at the best possible price through a random bidding mechanism. | |
| Adverse consequences and assessments | The effort concentrated on exchange power, giving precedence to those who have more bitcoin. The network nevertheless reveals a small bias. | |
| Final conclusion | The suggested profit approach was compared with PETCON through simulations carried out by the researchers using MATLAB and Solidity. The outcomes demonstrated the viability of the suggested strategy. | |
| MengShen [157], 2021 | Insightful depiction | BC made use of unintentional property leaking to allow FL for intelligent edge computing. |
| Ensuing Detention | For intelligent edge computing, the researchers suggest a brandnew property inference approach in BC-assisted FL. In addition to developing an active technique to learn and identify individuals with specified qualities from model updates, the project investigates inadvertent property leakage. | |
| Adverse consequences and assessments | The computational cost and decreased accuracy of the attack model are two of the property inference attack’s drawbacks that are emphasized. These drawbacks result from the assault model’s numerous iterations and the players’ more stringent selection criteria. | |
| Final conclusion | The researchers suggested an original approach for intelligent edge computing in BC-assisted FL that makes use of the accidental leaking of features from model updates. |
TABLE IV
| Author and Publication Year | Perspective | Description |
|---|---|---|
| Haoye Chai [158], 2021 | Insightful depiction | FL with BC activated for IoV knowledge transfer. |
| Ensuing Detention | In order to facilitate information exchange, this article presents a hierarchical BC architecture and FL algorithm. Vehicles use ML techniques to gather environmental data and share what they have learned with other vehicles. | |
| Adverse consequences and assessments | Analyzing the overhead and transaction throughput of the suggested hierarchical BCT is crucial in an Internet of Vehicles environment. This study sheds light on how the system is actually implemented in practice. | |
| Final conclusion | The results of the simulation show that the suggested hierarchical strategy improves the quality of learning and sharing effectiveness. Furthermore, the network of facilities provided by BC exhibits strong resilience across a range of hostile assaults. | |
| Weishan Zhang [159], 2021 | Insightful depiction | BC-based FL for IIoT failures in devices |
| Ensuing Detention | The research uses a Merkle tree for maintaining data integrity and BC-based FL for IIoT device failure identification. To deal with variability in the data and take into consideration varying class distances, a centroid distance-weighted federated averaging approach is utilized. | |
| Adverse consequences and assessments | The research work is restricted to the client-server architecture and does not address the possibility of moving the client-server to a client-side device, which is a topic that has not yet been investigated. | |
| Final conclusion | The research suggested a BC enabled FL method for IIoT equipment failure detection. The precise identification is made possible by the control server coordinating client servers to develop a worldwide framework utilizing normally acquired unprocessed information | |
| Sizheng Fan [160], 2021 | Insightful depiction | Edge computing using hybrid BC for resource trading. |
| Ensuing Detention | The researchers propose a hybrid resource marketplace for British Columbia that combines consortium and public BC. Edge node automatic reverse auctions are made possible by an intelligent contract. | |
| Adverse consequences and assessments | Additional research and focus will be needed to expand the suggested study to examine trading marketplaces with many requesters. | |
| Final conclusion | The researchers provide a resource trading system for FL in edge computing that is based on hybrid BC. Researchers suggest an automated and auditable reverse auction platform for edge nodes called data quality-driven reverse auctions (DQDRA), which makes use of a consortium BC smart contract. The outcomes of the simulation demonstrate DQDRA’s advantage over current reverse auction platforms. | |
| Hong Liu [161], 2021 | Insightful depiction | Using BC and FL to identify intrusions in-vehicle edge computing. |
| Ensuing Detention | The training model is transferred to edge equipment using the study’s decentralized cooperative intrusion detection technique. With confidentiality and anonymity preserved, the method lowers the central server’s resource consumption. | |
| Adverse consequences and assessments | Because of training models, offloading aggregation, and high storage needs, BC in-vehicle communication networks could face storage constraints. | |
| Final conclusion | The research looks at existing vulnerabilities and demonstrates how the suggested method preserves cooperative privacy while using less computing and communication overhead. |
TABLE V
| Author and Publication Year | Perspective | Description |
|---|---|---|
| Muhammad Shayan [162], 2021 | Insightful depiction | Leveraging BC and cryptography approaches, the study uses a decentralized P2P multiparty ML solution to provide securely protected ML processes among cooperating clients. |
| Ensuing Detention | The research identifies drawbacks of the suggested methodology, including leveraging large samples in a decentralized network, and scaling up to large models based on DL. | |
| Adverse consequences and assessments | The research shows that the suggested work is secure across known risks, extremely flexible, and fault-tolerant. | |
| Maninderpal Singh [163], 2021 | Insightful depiction | DL-driven BC in the context of the drone internet. |
| Ensuing Detention | In order to ensure safe information, the article suggests a powered BC authentication system for cyber-physical networks. | |
| Adverse consequences and assessments | The decrease in BC capacity of individual drones is not well covered in the report, indicating a potential field for more research. | |
| Final conclusion | The research puts forth a secure device-to-device and device-toeverything communication architecture using BC technology to guarantee safe data distribution. | |
| Zeinab Shahbazi [164], 2022 | Insightful depiction | Event detection is predicated on BC and validation of trust using ML exploration. |
| Ensuing Detention | The goal of this research project is to provide a disaster and emergency management platform. | |
| Adverse consequences and assessments | Generalization is difficult due to character constraints, internal language, and acronyms in microbiology. | |
| Final conclusion | To connect catastrophes and calamities to patient care organizations and enable effective relief activities, a continuous BC and ML pipeline is suggested. | |
| Taras Maksymyk [165], 2022 | Insightful depiction | Service management for the Decentralized Metaverse of Things based on BC technology. |
| Ensuing Detention | The study presents a paradigm for future metaverse applications with numerous synchronized data flows. | |
| Adverse consequences and assessments | Given the issues posed by the ambient pandemic, virtual and augmented reality will be more important. | |
| Final conclusion | In a decentralized mobile network context, the suggested method is based on dynamic fine-grained data flow allocation. | |
| Anant Singh Rajawat [166], 2023 | Insightful depiction | Deep Learning and BC for Securing 5G Enabled IoNT in a Big Data Environment. |
| Ensuing Detention | The authors develop a secure 5G Internet of Nano Things connection protocol. | |
| Adverse consequences and assessments | The physical layer (PHY) in 5G is more reliable than present AI algorithms but still provides flexibility, agility, and security. | |
| Final conclusion | The suggested paradigm includes a BC-secured 5G interface and AI-based quantum Boltzmann machines. |
TABLE VI
| Author and Publication Year | Perspective | Description |
|---|---|---|
| Dai [167] | Insightful depiction | BC-based FL-oriented Deep Reinforcement Learning for Resource Allocation |
| Ensuing Detention | The authors suggest a credit-based BC-enabled FL to jointly execute FL training and BC establishment. Secondly, they develop the idea of resource allocation by taking into account credit, data quality, preciseness, latency, and energy resources. An algorithm utilizing deep reinforcement learning is created to solve the problem, and BlockSim is utilized to construct the BC-enabled FL platform. | |
| Adverse consequences and assessments | Designing a fine-grained resource allocation scheme for BCenabled FL while taking into account the credit of devices, data quality, and energy resources. | |
| Final conclusion | The proposed simulation results show the effectiveness of our suggested approach on precision, latency, and energy consumption, compared with traditional BC-enabled FL. | |
| Sizhang Fan [168] | Insightful depiction | A dynamic game perspective for Mobile Devices Strategies in BCoriented FL |
| Ensuing Detention | The authors develop a BC-based FL system particularly the discrete strategy model and the continuous strategy model as two strategy models for mobile devices and interactions between the non-cooperative mobile devices as a dynamic game, in which each one repeatedly modifies its strategy to maximize its own reward in light of the strategies of the others. | |
| Adverse consequences and assessments | Two essential components are a fair trade platform and an incentive system to economically stimulate the involvement of diverse mobile devices. | |
| Final conclusion | The outcomes of the simulations validate the convergence of the suggested algorithms and indicate that, in comparison to DSM, the CSM may efficiently raise the payoffs for mobile devices to a maximum of 128 percent. | |
| Luo [169] | Insightful depiction | Enhancing the energy efficacy for intelligent BC Sharding Schemeoriented PBFT Consensus |
| Ensuing Detention | The authors suggest green sharding (GS), a sharding strategy that reduces energy usage for practical Byzantine fault tolerance (PBFT) consensus, as a solution to this problem. To make the computation of energy consumption for shared wireless BC networks easier, they also suggest a technique for estimating energy consumption following sharding. | |
| Adverse consequences and assessments | To further reduce the energy consumption of committee consensus on the GS basis. | |
| Final conclusion | The simulation results show that the GS is successful in reducing energy usage by 99.76%, and our estimation approach has a minimal error of only 0.11%. |
J. Future Work
Future research still needs to address the technological challenges of AI and BC. Regarding performance metrics, security, stability, and other factors, we can thoroughly examine the matching and cooperative optimization of next-generation networks driven by AI and BC. Furthermore, by doing additional research, we can guarantee BC and AI technologies’ robust and long-term advancement in next-generation networks. Consequently, we will concentrate on merging BC with AI to achieve better and more dispersed evolving wireless resource allocation. The coming decades might utilize novel sophisticated technologies that include cloud computing, edge computing, and big data to accelerate the advancement of BC and AI technologies. As a result, mutually beneficial development and the convergence of BC, AI, and the next generation constitute one of the main research paths for the decades to come. The upcoming incorporation of BC and AI is expected to be more comprehensive, and the instances used in next-generation networks will be broader. Integrating BC and AI in next-generation networks will result in novel discoveries and opportunities. This section outlines the open issues and research challenges associated with integrating BC and AI in next-generation wireless communications. In the future, research should hinge on creating innovative approaches to make BC more energy-efficient and scalable and investigating methods to safeguard privacy and security. It is also necessary to design effective data management systems and cross-layer AI protocols to handle AI-related difficulties. Prospective studies should focus on overcoming technological obstacles and uncertainties, promoting mutual promotion and integration, and investigating real-world applications. The integration of BC and AI for next-generation networks is still in its early phases. Overcoming these obstacles and advancing the integration of BC and AI in next-generation networks will significantly progress wireless communications.
VI. A COHESIVE UTILIZATION OF AI AND BC IN NEXT-GENERATION COMMUNICATION TECHNOLOGIES
A. AI and BC Unified Next generation-Molecular Communication Network
The advent of molecular communication as a prospective wireless network technology remains in its early stages. However, concerns surrounding authentication and communication processes in molecular communication have raised significant security and privacy issues, including data leakage and tampering between transmitters and recipients. These security threats span signaling, transport, link, and network layer attacks. In [178], molecular communication and nanotechnology convergence introduces an Internet of BioNano Things (IoBNT) application for online assessment of illness biomarkers utilizing molecular communication and ML techniques. Addressing security in molecular communication, studies [179] discuss black holes and sentry attacks impacting localization tasks, while eavesdroppers disrupt network reliability. The exploration of molecular communication and nano-electromagnetic communication [180] highlights challenges in data rate, reliability, and security levels. Abnormality detection in WSNs using electromagnetic waves [181] faces privacy risks from bio-cyber attacks. To counter these challenges, integrating BC into molecular communication networks proves pivotal, fortifying data privacy, and trust establishment, and providing secure communication and transactional frameworks. This integration bolsters privacy [182].
B. AI and BC Unified Next generation- Holographic Communication Network
Holographic Communication in next-generation networks promises immersive 3D experiences but raises concerns about security threats like hologram spoofing, replay attacks, and data manipulation. Safeguarding against these requires intelligent and adaptive technologies. Studies on reconfigurable holographic surfaces [183] emphasize fading effects impacting pattern integrity. Proposed holographic-pattern division multiple access [184] presents advantages but also vulnerabilities to collisions, interference, and unauthorized access. MIMO-oriented holographic communication [185] highlights open challenges in holographic channel estimation, robust beamforming, and security issues. The concept of multi-user holographic MIMO surfaces (MU-HMIMOS) [186] emphasizes energy efficiency but lacks robust channel modeling. Holographic communication for augmented reality and virtual reality [187] introduces latency challenges and the need for decentralized safeguards. Security vulnerabilities in human, machine, and metaverse communication are noted [188], emphasizing the need for real-time security measures. Radio localization’s significance and the prospect of holographic localization [189] introduce decentralized data storage to enhance network awareness and statistics. The integration of BC with holographic communication addresses privacy and security concerns by enhancing data privacy, trust, and security frameworks for communication and transactions. Extending this integration to next-generation networks becomes essential for efficient network management, privacy, and security in wireless communication systems. Integrating AI with BC enables intelligent learning, decentralized network updates, and adaptive wireless communications, optimizing network operations based on real-time data.
C. AI and BC Unified Next Generation- Semantic Communication Network
Claude Shannon’s information theory limits present a problem in the quest for ultra-high data speeds and extremely low latency in next-generation wireless communication networks. semantic communication setups have outperformed as a possible solution, utilizing knowledge Graph-based assessment to decrease uncertain semantics and errors. For instance, a study developed an semantic communication system optimizing bandwidth usage during image transmission [190] but encountered security challenges in noisy channels, necessitating error mitigation techniques. An in-depth investigation highlighted security issues with wireless environments, such as fading channels and constrained network resources [191]. Heterogeneous network devices constrain efficiency, emphasizing the need for Secure and efficient resource allocation and administration to reduce avoidable use of resources and preserve a reasonable bit error rate (BER). Exploring mechanisms for one-to-many semantic communication [192], [193] for broadcasting scenarios revealed interference challenges, advocating decentralized user identities to mitigate interference. Efforts in semantic data and wireless RA information extraction to improve the efficiency of energy in wireless communication [142], [143] face challenges concerning semantic information leakage, data integrity, and tamper-proof mechanisms [194]. The constraints on next-generation technology, limited by base station installations, call for Virtual adaptability to get around physical obstacles. In addition, issues with virtual reality deployment over wireless networks [141] include security issues. Nevertheless, modern studies’ lack of thorough security mechanisms keeps vulnerabilities unaddressed, such as interference, eavesdropping, semantically driven counterfeiting, and data leaking. The integrated approach of BC and AI is essential to mitigating these vulnerabilities in security. Although BC guarantees safe transactions and decentralized trust, AI enables intelligent identification of threats and flexible security strategies. By establishing a strong security framework, this convergence improves the privacy of confidential information and wireless networks.
VII. CONCLUSION
The main focus of the research was how to incorporate AI and BC with next-generation wireless technology. It emphasizes the necessity of proactive network administration considering the heterogeneous nature of networks and the demands of users. The exploration delves into the utilization of ML in next-generation across conventional and contemporary media communication, as well as in the next-generation IoT network. This review paper scrutinizes integrated sensing and communication networks, next-generation radar-based communication, RIS, visible light communication, RSMA, and BC’s application in spectrum reframing, Furthermore, it intricately examines the collaboration and impact of AI and BC on wireless communication networks, presenting unique characteristics such as intelligence, decentralized, confidential information. Additionally, model sharing is necessary for wireless communication networks. It elaborates on the combined use of AI and BC in cutting-edge next-generation communication technologies, such as semantic, holographic, and molecular communication. The investigation discusses unresolved problems, research obstacles, and options for integrating AI and BC in next-generation wireless networks. This survey provides an extensive understanding of wireless networks’ combined AI and BC strategy, promoting network security, decentralization, intelligence, self-sufficiency, and dependability.
Biography
Vuppula Roopa
Vuppula Roopa received the B.Tech. degree in electronics and communication engineering from Jyothismathi Institute of Technology and Science and the M.Tech degree in systems and signal processing from Jawaharlal Nehru Technological University, India, in 2015 and 2019, respectively. She is currently pursuing a Ph.D. degree at the National Institute of Technology in Warangal, India. Her research interests include wireless communications, resource allocation, Blockchain technology, and deep learning.
Biography
Himansu Shekhar Pradhan
Himansu Shekhar Pradhan (IEEE Member) received his Ph. D. degree from the Indian Institute of Technology Bhubaneswar, Odisha, India in the year 2017. He is a professional member of IEEE and is Currently, working as an Assistant Professor in the Electronics and Communication Engineering department at National Institute of Technology Warangal. His research interests include fiber optic sensor design and optimization, next-generation networks with AI and ML, SPR-based biomedical sensors, distributed fiber sensors, optical communication and sensing, characterization of optoelectronics devices, and optical signal processing
References
- 1 S. et al., "What should 6G be?" Nat. Electron., vol. 3, no. 1, pp. 20-29, 2020.custom:[[[-]]]
- 2 P. Yang et al., "6G wireless communications: Vision and potential techniques," IEEE Netw., vol. 33, no. 4, pp. 70-75, 2019.custom:[[[-]]]
- 3 F. Tariq et al., "A speculative study on 6G," IEEE Wireless Commun., vol. 27, no. 4, pp. 118-125, 2020.custom:[[[-]]]
- 4 W. Jiang et al., "The road towards 6G: A comprehensive survey," IEEE Open J. Commun. Soc., vol. 2, pp. 334-366, 2021.custom:[[[-]]]
- 5 Z. Zhang. et al., "6G wireless networks: Vision, requirements, architecture, and key technologies," IEEE Veh. Technol. Mag., vol. 14, no. 3, pp. 28-41, 2019.custom:[[[-]]]
- 6 D. C. Nguyen. et al., "6G internet of things: A comprehensive survey," IEEE Internet Things J., vol. 9, no. 1, pp. 359-383, 2022.custom:[[[-]]]
- 7 W. Saad, M. Bennis, and M. Chen, "A vision of 6G wireless systems: Applications, trends, technologies, and open research problems," IEEE Netw., vol. 34, no. 3, pp. 134-142, 2019.custom:[[[-]]]
- 8 M. Z. Chowdhury et al., "6G wireless communication systems: Applications, requirements, technologies, challenges, and research directions," IEEE Open J. Commun. Soc., vol. 1, pp. 957-975, 2020.custom:[[[-]]]
- 9 N. Kato et al., "Ten challenges in advancing ML technologies toward 6G," IEEE Wireless Commun., vol. 27, no. 3, pp. 96-103, 2020.custom:[[[-]]]
- 10 H. Yang et al., "Artificial-intelligence-enabled intelligent 6G network," IEEE Netw., vol. 34, no. 6, pp. 272-280, 2020.custom:[[[-]]]
- 11 S. Khan et al., "Efficient and reliable hybrid deep learning-enabled model for congestion control in 5G/6G networks," Comput. Commun., vol. 182, pp. 31-40, 2022.custom:[[[-]]]
- 12 J. Guo, Y . Zuo, and C. K. Wen, "User-centric online gossip training for autoencoder-based csi feedback," IEEE J. Sel. Topics Signal Process., vol. 16, no. 3, pp. 559-572, 2022.custom:[[[-]]]
- 13 J. Guo, C. K. Wen, and S. Jin, "Ca-net: Uplink-aided downlink channel acquisition in fdd massive mimo using deep learning," IEEE Trans. Commun., vol. 70, no. 1, pp. 199-214, 2022.custom:[[[-]]]
- 14 M. L. Aho et al., "Key drivers and research challenges for 6G ubiquitous wireless intelligence (white paper)," 2019, available: http://urn.fi/urn:isbn:9789526223544.custom:[[[http://urn.fi/urn:isbn:9789526223544]]]
- 15 S. ITU, GENEV A, "Framework for evaluating intelligence levels of future networks including imt-2020," 2020, dOI: https://www.itu.int/rec/T-REC-Y .3173/en.custom:[[[https://www.itu.int/rec/T-REC-Y.3173/en]]]
- 16 J. Leng et al., "BC security: A survey of techniques and research directions," IEEE Trans. Services Comput., vol. 15, no. 4, pp. 2490-2510, 2022.custom:[[[-]]]
- 17 M. Wang et al., "Security and privacy in 6G networks: New areas and new challenges," Digit. Commun. Netw., vol. 6, no. 3, pp. 281-291, 2020.custom:[[[-]]]
- 18 M. Conti et al., "A survey on security and privacy issues of bitcoin," IEEE Commun. Surveys Tuts., vol. 20, no. 4, pp. 3416-3452, 4th Quart.custom:[[[-]]]
- 19 T. Hewa et al., "The role of BC in 6G: Challenges, opportunities, and research directions," in Proc. 6G SUMMIT, Levi, Finland, pp. 1-5, 2020.custom:[[[-]]]
- 20 Y . Zhu, G. Zheng, and K. K. Wong, "BC-empowered decentralized storage in air-to-ground industrial networks," IEEE Trans. Ind. Informat., vol. 15, no. 6, pp. 3593-3601, 2019.custom:[[[-]]]
- 21 A. Pradhan, S. Das, M. J. Piran, and Z. Han, "A survey on physical layer security of ultra/hyper reliable low latency communication in 5G and 6G networks: Recent advancements, challenges, and future directions," IEEE Access, vol. 12, pp. 112320-112353, 2024.custom:[[[-]]]
- 22 Y . Yuan et al., "BC technology: From data intelligence to knowledge automation," Acta Automatica Sinica, vol. 43, no. 9, pp. 1485-1490, 2017.custom:[[[-]]]
- 23 K. D. Pandl, S. Thiebes, and A. Sunyaev, "On the convergence of AI and distributed ledger technology: A scoping review and future research agenda," IEEE Access, vol. 8, pp. 57075-57095, 2020.custom:[[[-]]]
- 24 T. N. Dinh and M. T. Thai, "AI and BC: A disruptive integration," Computer, vol. 51, no. 9, pp. 48-53, 2018.custom:[[[-]]]
- 25 S. K. Singh, S. Rathore, and J. Park, "BlockIoTintelligence: A BCenabled intelligent IoT architecture with AI," Future Gener. Comput. Syst., vol. 102, pp. 414-429, 2020.custom:[[[-]]]
- 26 B. Xing and T. Marwala, "The synergy of BC and AI," in Proc. SSRN, 2018.custom:[[[-]]]
- 27 T. N. Dinh and M. T. Thai, "AI and BC: A disruptive integration," Computer, vol. 51, no. 9, pp. 48-53, 2018.custom:[[[-]]]
- 28 M. Wu, K. Wang, and E. A. X. Cai, "A comprehensive survey of BC: From theory to IoT applications and beyond," IEEE Internet Things J., vol. 6, no. 5, pp. 8114-8154, 2019.custom:[[[-]]]
- 29 K. Salah et al., "BC for AI: Review and open research challenges," IEEE Access, vol. 7, pp. 10127-10149, 2019.custom:[[[-]]]
- 30 S. S. Gill et al., "Transformative effects of IoT, BC, and AI on cloud computing: Evolution, vision, trends and open challenges," Internet Things, vol. 8, 2019.custom:[[[-]]]
- 31 D. C. Nguyen et al., "BC for 5G and beyond networks: A state of the art survey," J. Netw. Comput. Appl., vol. 166, Sep. 2020.custom:[[[-]]]
- 32 Y . Liu et al., "BC and ML for communications and networking systems," IEEE Commun. Surveys Tuts., vol. 22, no. 2, pp. 1392-1431, 2nd Quart. 2020.custom:[[[-]]]
- 33 F. Jameel et al., "Reinforcement learning in BC-enabled iIoT networks: A survey of recent advances and open challenges," Sustainability, vol. 12, no. 12, p. 5161, 2020.custom:[[[-]]]
- 34 B. K. Ohanta et al., "Survey on IoT security: Challenges and solution using ML, AI, and BC technology," Internet Things, vol. 11, 2020.custom:[[[-]]]
- 35 A. E. Azzaoui et al., "Block5Gintell: BC for AI-enabled 5G networks," IEEE Access, vol. 8, pp. 145918-145935, 2020.custom:[[[-]]]
- 36 K. D. Pandl et al., "On the convergence of AI and distributed ledger technology: A scoping review and future research agenda," IEEE Access, vol. 8, pp. 57075-57095, 2020.custom:[[[-]]]
- 37 S. K. Singh, S. Rathore, and J. H. Park, "BlockIoTintelligence: A BCenabled intelligent IoT architecture with AI," Future Gener. Comput. Syst., vol. 110, pp. 721-743, 2020.custom:[[[-]]]
- 38 Y . Liu et al., "Federated learning for 6G communications: Challenges, methods, and future directions," China Commun., vol. 17, no. 9, pp. 105-118, 2020.custom:[[[-]]]
- 39 M. Lin and Y . Zhao, "AI-empowered resource management for future wireless communications: A survey," China Commun., vol. 17, no. 3, pp. 58-77, 2020.custom:[[[-]]]
- 40 M. Tahir et al., "A review on application of BC in 5G and beyond networks: Taxonomy, field-trials, challenges and opportunities," IEEE Access, vol. 8, pp. 115876-115904, 2020.custom:[[[-]]]
- 41 S. A. Bhat, I. B. Sofi, and C. Y . Chi, "Edge computing and its convergence with BC in 5G and beyond: Security, challenges, and opportunities," IEEE Access, vol. 8, pp. 205340-205373, 2020.custom:[[[-]]]
- 42 Y . Sun, J. Liu, and J. Wang, "When ML meets privacy in 6G: A survey," IEEE Commun. Surveys Tuts., vol. 22, no. 4, pp. 2694-2724, 2020.custom:[[[-]]]
- 43 K. Yue et al., "A survey of decentralizing applications via BC: The 5G and beyond perspective," IEEE Commun. Surveys Tuts., vol. 23, no. 4, pp. 2191-2217, 2021.custom:[[[-]]]
- 44 P. Sharma et al., "Role of ML and deep learning in securing 5G-driven industrial IoT applications," Ad Hoc Netw., vol. 123, 2021.custom:[[[-]]]
- 45 J. Wang, X. Ling, and Y . Le, "BC-enabled wireless communications: A new paradigm towards 6G," Nat. Sci. Rev., vol. 8, no. 9, 2021.custom:[[[-]]]
- 46 V . P. Rekkas et al., "ML in beyond 5G/6G networks-state-of-the-art and future trend," Electronics, vol. 10, no. 22, p. 2786, 2021.custom:[[[-]]]
- 47 R. Wang, M. Luo, and Y . Wen, "The applications of BC in AI," Security Commun. Netw., vol. 2021, Sep. 2021. (Online). Available: https://www.hindawi.com/journals/scn/2021/6126247/custom:[[[-]]]
- 48 A. Hussain and Man, "AI and BC: A review," Trans. Emerg. Telecommun. Technol., vol. 32, no. 9, 2021.custom:[[[-]]]
- 49 P. Tagde et al., "BC and AI technology in e-health," Environ. Sci. Pollution Res., vol. 28, pp. 52810-52831, 2021.custom:[[[-]]]
- 50 A. D. Dwivedi et al., "BC and AI for 5G-enabled internet of things: Challenges, opportunities, and solutions," Trans. Emerg. Telecommun. Technol., 2021.custom:[[[-]]]
- 51 Y . Wu et al., "Deep reinforcement learning for BC in industrial IoT: A survey," Comput. Netw., vol. 191, p. 108004, 2021.custom:[[[-]]]
- 52 K. Miglani and N. Kumar, "BC management and ML adaptation for IoT environment in 5G and beyond networks: A systematic review," Comput. Commun., vol. 178, pp. 37-63, 2021.custom:[[[-]]]
- 53 M. Dibaei et al., "Investigating the prospect of leveraging BC and ML to secure vehicular networks: A survey," IEEE Trans. Intell. Transp. Syst., vol. 23, no. 2, pp. 683-700, 2022.custom:[[[-]]]
- 54 M. Shafay et al., "BC for deep learning: Review and open challenges," Clust. Comput., vol. 26, pp. 197-221, 2022.custom:[[[-]]]
- 55 Q. Yang et al., "Fusing BC and AI with metaverse: A survey," IEEE Open J. Comput. Soc., vol. 3, pp. 122-136, 2022.custom:[[[-]]]
- 56 X. Li et al., "BC-oriented applications in next-generation wireless systems: Challenges and opportunities," IEEE Wireless Commun., vol. 28, no. 2, pp. 86-95, 2021.custom:[[[-]]]
- 57 J. Kwon, D. Jung, and H. Park, "Traffic data classification using ML algorithms in sdn networks," in Proc. ICTC, pp. 1031-1033, 2020.custom:[[[-]]]
- 58 S. M. Rachmawati, D. S. Kim, and J. M. Lee, "ML algorithm in network traffic classification," in Proc. ICTC, pp. 1010-1013, 2021.custom:[[[-]]]
- 59 R. G´ omez et al., "Machine-learning based traffic forecasting for resource management in c-ran," in Proc. EuCNC, pp. 200-204, 2024.custom:[[[-]]]
- 60 J. Huang et al., "A big data oriented channel model for 5G wireless communication systems," IEEE Trans. Big Data, vol. 6, no. 2, pp. 211-222, 2020.custom:[[[-]]]
- 61 S. Goodarzy et al., "Resource management in cloud computing using ML: A survey," pp. 811-816, 2020.custom:[[[-]]]
- 62 A. Alnoman, "ML-based task clustering for enhanced virtual machine utilization in edge computing," pp. 1-4, 2020.custom:[[[-]]]
- 63 Z. Lv et al., "Big data analytics for 6G-enabled massive internet of things," IEEE Internet Things J., vol. 8, no. 7, pp. 5350-5359, 2021.custom:[[[-]]]
- 64 A. Gandomi and M. Haider, "Beyond the hype: Big data concepts, methods, and analytics," Int. J. Inf. Manage., vol. 35, no. 2, pp. 137-144, 2015.custom:[[[-]]]
- 65 X. Cheng et al., "Exploiting mobile big data: Sources, features, and applications," IEEE Netw., vol. 31, no. 1, pp. 72-79, 2017.custom:[[[-]]]
- 66 S. Maran` o et al., "Nlos identification and mitigation for localization based on uwb experimental data," IEEE J. Sel. Areas Commun., vol. 28, no. 7, pp. 1026-1035, 2010.custom:[[[-]]]
- 67 T. V . Nguyen et al., "Machine learning for wideband localization," IEEE J. Sel. Areas Commun., vol. 33, no. 7, pp. 1357-1380, 2015.custom:[[[-]]]
- 68 H. Zou et al., "A robust indoor positioning system based on the procrustes analysis and weighted extreme learning machine," IEEE Trans. Wireless Commun., vol. 15, no. 2, pp. 1252-1266, 2016.custom:[[[-]]]
- 69 X. Liang et al., "Extreme learning machine for 60 Ghz millimetre wave positioning," IET Commun., vol. 11, no. 4, pp. 483-489, 2017.custom:[[[-]]]
- 70 K. M. Thilina et al., "Machine learning techniques for cooperative spectrum sensing in cognitive radio networks," IEEE J. Sel. Areas Commun., vol. 31, no. 11, pp. 2209-2221, 2013.custom:[[[-]]]
- 71 D. He et al., "Transmit antenna selection in mimo wiretap channels: A machine learning approach," IEEE Wireless Commun. Lett., vol. 7, no. 4, pp. 634-637, 2018.custom:[[[-]]]
- 72 K. B. Letaief et al., "The roadmap to 6G: AI empowered wireless networks," IEEE Commun. Mag., vol. 57, no. 8, pp. 84-90, 2019.custom:[[[-]]]
- 73 K. David and H. Berndt, "6G vision and requirements: Is there any need for beyond 5G?" IEEE Veh. Technol. Mag., vol. 13, no. 3, pp. 72-80, Sep. 2018.custom:[[[-]]]
- 74 Y . Xiao et al., "Towards ubiquitous AI in 6G with federated learning," 2020, arXiv:2004.13563.custom:[[[-]]]
- 75 J. Koneˇ cn´ y et al., "Federated learning: Strategies for improving communication efficiency," 2016, arXiv:1610.05492.custom:[[[-]]]
- 76 J. Kang et al., "Incentive mechanism for reliable federated learning: A joint optimization approach to combining reputation and contract theory," IEEE Internet Things J., vol. 6, no. 6, pp. 10700-10714, 2019.custom:[[[-]]]
- 77 Zhang et al., "The impact of artificial intelligence and blockchain on the accounting profession," IEEE Access, vol. 8, pp. 110461-110477, 2020.custom:[[[-]]]
- 78 J. Li, R. Qin, S. Guan, J. Hou, and F.-Y . Wang, "Blockchain intelligence: Intelligent blockchains for web 3.0 and beyond," IEEE Trans. Syst., Man, Cybernetics: Syst., 2024.custom:[[[-]]]
- 79 X. Zhang et al., "Spectral efficiency improvement and power control optimization of massive mimo networks," IEEE Access, vol. 9, pp. 11523-11532, 2021.custom:[[[-]]]
- 80 Y . Lu et al., "Semi-supervised machine learning aided anomaly detection method in cellular networks," IEEE Trans. Veh. Technol., vol. 69, no. 8, pp. 8459-8467, 2020.custom:[[[-]]]
- 81 A. B. Nassif et al., "Machine learning for anomaly detection: A systematic review," IEEE Access, vol. 9, pp. 78658-78700, 2021.custom:[[[-]]]
- 82 M. F. Kucuk and I. Uysal, "Anomaly detection in self-organizing networks: Conventional versus contemporary machine learning," IEEE Access, vol. 10, pp. 61744-61752, 2022.custom:[[[-]]]
- 83 S. Naseer et al., "Enhanced network anomaly detection based on deep neural networks," IEEE Access, vol. 6, pp. 48231-48246, 2018.custom:[[[-]]]
- 84 H. W. Oleiwi et al., "Mlts-adcns: Machine learning techniques for anomaly detection in communication networks," IEEE Access, vol. 10, pp. 91006-91017, 2022.custom:[[[-]]]
- 85 S. Wang et al., "Machine learning in network anomaly detection: A survey," IEEE Access, vol. 9, pp. 152379-152396, 2021.custom:[[[-]]]
- 86 J. Kwon et al., "Traffic data classification using machine learning algorithms in sdn networks," in Proc. ICTC, pp. 1031-1033, 2020.custom:[[[-]]]
- 87 S. M. Rachmawati et al., "Machine learning algorithm in network traffic classification," in Proc. ICTC, pp. 1010-1013, 2021.custom:[[[-]]]
- 88 A. R. Deshmukh and S. S. Dorle, "Bio-inspired optimization algorithms for improvement of vehicle routing problems," in Proc. ICETET, pp. 14-18, 2015.custom:[[[-]]]
- 89 S. Shakya and S. R. Pokhrel, "Global optimization of field based routing in wireless mesh network (gofbr-wmn)," in Proc. 3rd Asian Himalayas Int. Conf. Internet, pp. 1-5, 2012.custom:[[[-]]]
- 90 A. V . da Silva and G. S. Pavani, "Tackling multiple byzantine failures in optical networks routed by means of ant colony optimization," in Proc. ICTON, pp. 1-4, 2019.custom:[[[-]]]
- 91 S. Xu, X. Wang, G. Yang, J. Ren, and S. Wang, "Routing optimization for cloud services in sdn-based internet of things with tcam capacity constraint," J. Commun. Netw., vol. 22, no. 2, pp. 145-158, 2020.custom:[[[-]]]
- 92 S. R. Pokhrel and S. Shakya, "Enhanced optimization of field based routing for macro mobility in IEEE 802.11s mesh," in Proc. WOCN, pp. 1-5, 2013.custom:[[[-]]]
- 93 T. L. Lin, Y . S. Chen, and H. Y . Chang, "Performance evaluations of an ant colony optimization routing algorithm for wireless sensor networks," in Proc. 10th Int. Conf. Intell. Inf. Hiding Multimedia Signal Process., pp. 690-693, 2014.custom:[[[-]]]
- 94 R. Guerra-G´ omez, S. R. Boqu´ e, M. Garc´ ıa-Lozano, and J. O. Bonaf´ e, "Machine-learning based traffic forecasting for resource management in c-ran," in Proc. EuCNC, pp. 200-204, 2020.custom:[[[-]]]
- 95 S. Goodarzy, M. Nazari, R. Han, E. Keller, and E. Rozner, "Resource management in cloud computing using machine learning: A survey," in Proc. ICMLA, pp. 811-816, 2020.custom:[[[-]]]
- 96 A. Alnoman, "Machine learning-based task clustering for enhanced virtual machine utilization in edge computing," in Proc. CCECE, pp. 1-4, 2020.custom:[[[-]]]
- 97 R. Guerra-G´ omez, S. Ruiz-Boqu´ e, M. Garc´ ıa-Lozano, and J. O. Bonafe, "Machine learning adaptive computational capacity prediction for dynamic resource management in c-ran," IEEE Access, vol. 8, pp. 89130-89142, 2020.custom:[[[-]]]
- 98 W. Guo, W. Tian, Y . Ye, L. Xu, and K. Wu, "Cloud resource scheduling with deep reinforcement learning and imitation learning," IEEE Internet of Things J., vol. 8, no. 5, pp. 3576-3586, 2021.custom:[[[-]]]
- 99 S. Yu, X. Chen, Z. Zhou, X. Gong, and D. Wu, "When deep reinforcement learning meets federated learning: Intelligent multitimescale resource management for multiaccess edge computing in 5G ultradense network," IEEE Internet Things J., vol. 8, no. 4, pp. 2238-2251, 2021.custom:[[[-]]]
- 100 Y . He, "Research on the key technology of network security based on machine learning," in Proc. ICSP, pp. 972-975, 2021.custom:[[[-]]]
- 101 T. P. Anithaashri and G. Ravichandran, "Security enhancement for the network amalgamation using machine learning algorithm," in Proc. ICOSEC, pp. 411-416, 2020.custom:[[[-]]]
- 102 W. Yang, X. C. Yun, and L. J. Zhang, "Using incremental learning method for adaptive network intrusion detection," in Proc. Int. Conf. Mach. Learn. Cybern., vol. 7, pp. 3932-3936, 2005.custom:[[[-]]]
- 103 C.-C. Li, A.-L. Guo, and D. Li, "Application research of support vector machine in network security risk evaluation," in Proc. Int. Symp. Intell. Inf. Technol. Appl. Workshops, pp. 40-43, 2008.custom:[[[-]]]
- 104 W. Zhong, N. Yu, and C. Ai, "Applying big data based deep learning system to intrusion detection," Big Data Mining Anal., vol. 3, no. 3, pp. 181-195, 2020.custom:[[[-]]]
- 105 G. Pu, L. Wang, J. Shen, and F. Dong, "A hybrid unsupervised clusteringbased anomaly detection method," Tsinghua Sci. Technol., vol. 26, no. 2, pp. 146-153, 2021.custom:[[[-]]]
- 106 S. Otoum, B. Kantarci, and H. T. Mouftah, "On the feasibility of deep learning in sensor network intrusion detection," IEEE Netw. Lett., vol. 1, no. 2, pp. 68-71, 2019.custom:[[[-]]]
- 107 G. D. C. Bertoli, et al., "An end-to-end framework for machine learning-based network intrusion detection system," IEEE Access, vol. 9, pp. 106790-106805, 2021.custom:[[[-]]]
- 108 J. Lansky et al., "Deep learning-based intrusion detection systems: A systematic review," IEEE Access, vol. 9, pp. 101574-101599, 2021.custom:[[[-]]]
- 109 D. C. Nguyen, P. N. Pathirana, M. Ding, and A. Seneviratne, "Blockchain for 5G and beyond networks: A state of the art survey," J. Netw. Comput. Appl., vol. 166, p. Art. no. 102693, 2020.custom:[[[-]]]
- 110 S. Wijethilaka and M. Liyanage, "Survey on network slicing for internet of things realization in 5G networks," IEEE Commun. Surveys Tuts., vol. 23, no. 2, pp. 957-994, 2021, 2nd Quart.custom:[[[-]]]
- 111 V . A. Cunha et al., "5Growth: Secure and reliable network slicing for verticals," in Proc. EuCNC/6G Summit, pp. 347-352, 2021.custom:[[[-]]]
- 112 P. Du, A. Nakao, L. Zhong, and R. Onishi, "Intelligent network slicing with edge computing for internet of vehicles," IEEE Access, vol. 9, pp. 128106-128116, 2021.custom:[[[-]]]
- 113 A. Ksentini, M. Jebalia, and S. Tabbane, "Fog-enabled industrial IoT network slicing model based on ML-enabled multi-objective optimization," in Proc. WETICE, pp. 177-180, 2020.custom:[[[-]]]
- 114 J. Mei, X. Wang, and K. Zheng, "Intelligent network slicing for V2X services toward 5G," IEEE Netw., vol. 33, no. 6, pp. 196-204, 2019.custom:[[[-]]]
- 115 Y . Li and M. Chen, "Software-defined network function virtualization: A survey," IEEE Access, vol. 3, pp. 2542-2553, 2015.custom:[[[-]]]
- 116 G. Kibalya et al., "A reinforcement learning based approach for 5G network slicing across multiple domains," in Proc. CNSM, pp. 1-5, 2019.custom:[[[-]]]
- 117 H. A. Shah and L. Zhao, "Multiagent deep-reinforcement-learningbased virtual resource allocation through network function virtualization in internet of things," IEEE Internet Things J., vol. 8, no. 5, pp. 3410-3421, 2021.custom:[[[-]]]
- 118 S. Moazzeni et al., "A novel autonomous profiling method for the next-generation nfv orchestrators," IEEE Trans. Netw. Service Manage., vol. 18, no. 1, pp. 642-655, 2021.custom:[[[-]]]
- 119 Y . Zhao et al., "A survey of networking applications applying the software defined networking concept based on machine learning," IEEE Access, vol. 7, pp. 95397-95417, 2019.custom:[[[-]]]
- 120 P. Amaral et al., "Machine learning in software defined networks: Data collection and traffic classification," in Proc. ICNP, pp. 1-5, 2016.custom:[[[-]]]
- 121 W. Kellerer et al., "Adaptable and data-driven softwarized networks: Review, opportunities, and challenges," Proc. IEEE, vol. 107, no. 4, pp. 711-731, 2019.custom:[[[-]]]
- 122 R. Etengu, S. C. Tan, L. C. Kwang, F. M. Abbou, and T. C. Chuah, "AI-assisted framework for green-routing and load balancing in hybrid software-defined networking: Proposal, challenges and future perspective," IEEE Access, vol. 8, pp. 166384-166441, 2020.custom:[[[-]]]
- 123 M. Abderrahim, A. B. Letaifa, A. Haji, and S. Tabbane, "How to use mec and ML to improve resources allocation in sdn networks?" in Proc. WAINA, pp. 442-447, 2018.custom:[[[-]]]
- 124 A. R. Mohammed, S. A. Mohammed, and S. Shirmohammadi, "Machine learning and deep learning based traffic classification and prediction in software defined networking," in Proc. MN, pp. 1-6, 2019.custom:[[[-]]]
- 125 E. H. Bouzidi, A. Outtagarts, and R. Langar, "Deep reinforcement learning application for network latency management in software defined networks," in Proc. GLOBECOM, pp. 1-6, 2019.custom:[[[-]]]
- 126 S. Anbalagan et al., "Machine-learning-based efficient and secure rsu placement mechanism for software-defined-iov," IEEE Internet Things J., vol. 8, no. 18, pp. 13950-13957, 2021.custom:[[[-]]]
- 127 J. Aiken and S. Scott-Hayward, "Investigating adversarial attacks against network intrusion detection systems in sdns," in Proc. NFVSDN, pp. 1-7, 2019.custom:[[[-]]]
- 128 Y . Liu et al., "Reconfigurable intelligent surfaces: Principles and opportunities," IEEE Commun. Surveys Tuts., vol. 23, no. 3, pp. 1546-1547, 2021.custom:[[[-]]]
- 129 X. Fang et al., "Joint communication and sensing toward next generation: Models and potential of using mimo," IEEE Internet Things J., vol. 10, no. 5, pp. 4093-4116, 2023.custom:[[[-]]]
- 130 L. You et al., "Beam squint-aware integrated sensing and communications for hybrid massive mimo leo satellite systems," IEEE J. Sel. Areas Commun., vol. 40, no. 10, pp. 2994-3009, 2022.custom:[[[-]]]
- 131 X. Cheng et al., "Integrated sensing and communications (ISAC) for vehicular communication networks (VCN)," IEEE Internet Things J., vol. 9, no. 23, pp. 23441-23451, 2022.custom:[[[-]]]
- 132 Z. Du et al., "Integrated sensing and communications for V2I networks: Dynamic predictive beam forming for extended vehicle targets," IEEE Trans. Wireless Commun., vol. 22, no. 6, pp. 3612-3627, 2022.custom:[[[-]]]
- 133 T. Alladi et al., "A comprehensive survey on the applications of BC for securing vehicular networks," IEEE Commun. Surveys Tuts., vol. 24, no. 2, pp. 1212-1239, 2022.custom:[[[-]]]
- 134 E.-K. Hong et al., "6G vision: Requirements and candidate technologies," J. Commun. Netw., vol. 24, no. 2, pp. 232-245, 2022.custom:[[[-]]]
- 135 W. Li et al., "BC-based data security for AI applications in nextgeneration networks," IEEE Netw., vol. 34, no. 6, pp. 31-37, 2020.custom:[[[-]]]
- 136 C. Qiu et al., "Deep reinforcement learning empowered adaptivity for future BC networks," IEEE Open J. Comput. Soc., vol. 2, pp. 99-105, 2021.custom:[[[-]]]
- 137 V . Roopa and H. S. Pradhan, "BC oriented spectrum sharing in intelligent wireless networks," 2023.custom:[[[-]]]
- 138 R. Vuppula and P. H. Shekhar, "Blockchain based spectrum sensing for secured cognitive radio wireless networks," in CSNT. IEEE, pp. 553-559, 2022.custom:[[[-]]]
- 139 V . Roopa and H. S. Pradhan, "Smart contract implementation on network sharing for next generation wireless networks," Annals of Telecommunications, 2024.custom:[[[-]]]
- 140 R. Vuppula and H. S. Pradhan, "BC-oriented location privacypreserving for cooperative spectrum sensing in 6G wireless networks," IET Blockchain, vol. 3, no. 2, pp. 74-97, 2023.custom:[[[-]]]
- 141 V . Roopa and H. S. Pradhan, "Mathematical modeling and performance evaluation of beran for next-generation wireless networks," The J. Supercomputing, vol. 79, no. 15, pp. 16479-16528, 2023.custom:[[[-]]]
- 142 Leewayhertz, "What are the various BC scalability solutions?" https://www.leewayhertz.com/BC-scalability-solutions/, 2022.custom:[[[https://www.leewayhertz.com/BC-scalability-solutions/,2022]]]
- 143 D. Cheng et al., "Why dataset properties bound the scalability of parallel ML training algorithms," IEEE Trans. Parallel Distrib. Syst., vol. 32, no. 7, pp. 1702-1712, 2021.custom:[[[-]]]
- 144 F. H. Juwono et al., "Envisioning 6G molecular communication for iobnt diagnostic systems," in Proc. GECOST, pp. 1-5, 2021.custom:[[[-]]]
- 145 A. Etemadi et al., "Abnormality detection and localization schemes using molecular communication systems: A survey," IEEE Access, vol. 11, pp. 1761-1792, 2023.custom:[[[-]]]
- 146 W. Guo et al., "Molecular physical layer for 6G in wave denied environments," IEEE Commun. Mag., vol. 59, no. 5, pp. 33-39, 2021.custom:[[[-]]]
- 147 R. Deng et al., "Reconfigurable holographic surfaces for future wireless communications," IEEE Wireless Commun., vol. 28, no. 6, pp. 126-131, 2021.custom:[[[-]]]
- 148 ——, "Hdma: Holographic-pattern division multiple access," IEEE J. Sel. Areas Commun., vol. 40, no. 4, pp. 1317-1332, 2022.custom:[[[-]]]
- 149 H. Lee et al., "Towards 6G hyper-connectivity: Vision, challenges, and key enabling technologies," Journal of Communications and Networks, vol. 25, no. 3, pp. 344-354, 2023.custom:[[[-]]]
- 150 L. Wei et al., "Multi-user wireless communications with holographic mimo surfaces: A convenient channel model and spectral efficiency analysis," in Proc. EuCNC/next gen. Summit, pp. 488-493, 2022.custom:[[[-]]]
- 151 N. Petkov et al., "Comparative study of latent-sensitive processing of heterogeneous data in an experimental platform for 3d video holographic communication," in Proc. GCWOT, pp. 1-6, 2022.custom:[[[-]]]
- 152 I. F. Akyildiz, "Metaverse: Challenges for extended reality and holographic-type communication in the next decade," in Proc. ITU Kaleidoscope-Extended Reality Boost Quality Exp. Interoperability, pp. 1-2, 2022.custom:[[[-]]]
- 153 M. U. Lokumarambage et al., "Wireless end-to-end image transmission system using semantic communications," IEEE Access, vol. 11, pp. 37149-37163, 2023.custom:[[[-]]]
- 154 M. Maaroufi and S. Pierre, "Bcool: A novel BC congestion control architecture using dynamic service function chaining and machine learning for next-generation vehicular networks," IEEE Access, vol. 9, pp. 53096-53122, 2021.custom:[[[-]]]
- 155 A. Asheralieva and D. Niyato, "Bayesian reinforcement learning and bayesian deep learning for blockchains with mobile edge computing," IEEE Trans. Cogn. Commun. Netw., vol. 7, no. 1, pp. 319-335, 2021.custom:[[[-]]]
- 156 D. Said, "A decentralized electricity trading framework (detf) for connected evs: A BC and machine learning for profit margin optimization," IEEE Trans. Ind. Informat., vol. 17, no. 10, pp. 6594-6602, 2021.custom:[[[-]]]
- 157 M. Shen et al., "Exploiting unintended property leakage in BC-assisted federated learning for intelligent edge computing," IEEE Internet Things J., vol. 8, no. 4, pp. 2265-2275, 2021.custom:[[[-]]]
- 158 H. Chai et al., "A hierarchical BC-enabled federated learning algorithm for knowledge sharing in the internet of vehicles," IEEE Trans. Intell. Transp. Syst., vol. 22, no. 7, pp. 3975-3986, 2021.custom:[[[-]]]
- 159 W. Zhang et al., "BC-based federated learning for device failure detection in industrial IoT," IEEE Internet Things J., vol. 8, no. 7, pp. 5926-5937, 2021.custom:[[[-]]]
- 160 S. Fan et al., "Hybrid BC-based resource trading system for federated learning in edge computing," IEEE Internet Things J., vol. 8, no. 4, pp. 2252-2264, 2021.custom:[[[-]]]
- 161 H. Liu et al., "Blockchain and federated learning for collaborative intrusion detection in vehicular edge computing," IEEE Trans. Veh. Technol., vol. 70, no. 6, pp. 6073-6084, 2021.custom:[[[-]]]
- 162 M. Shayan et al., "Biscotti: A blockchain system for private and secure federated learning," IEEE Trans. Parallel Distrib. Syst., vol. 32, no. 7, pp. 1513-1525, 2021.custom:[[[-]]]
- 163 M. Singh, G. S. Aujla, and R. S. Bali, "A deep learning-based BC mechanism for secure internet of drones environment," IEEE Trans. Intell. Transp. Syst., vol. 22, no. 7, pp. 4404-4413, 2021.custom:[[[-]]]
- 164 Z. Shahbazi and Y . C. Byun, "BC-based event detection and trust verification using natural language processing and machine learning," IEEE Access, vol. 10, pp. 5790-5800, 2022.custom:[[[-]]]
- 165 T. Maksymyuk et al., "BC-empowered service management for the decentralized metaverse of things," IEEE Access, vol. 10, pp. 99025-99037, 2022.custom:[[[-]]]
- 166 S. Rajawat et al., "Deep learning and BC for securing 5G enabled iont in big data environment," in ICICT, Lalitpur, Nepal, pp. 1233-1240, 2023.custom:[[[-]]]
- 167 Y . Dai, H. Yang, and H. Yang, "Deep reinforcement learning for resource allocation in BC-based federated learning," in Proc. IEEE ICC, Rome, Italy, pp. 179-184, 2023.custom:[[[-]]]
- 168 S. Fan, et al., "Mobile devices strategies in BC-based federated learning: A dynamic game perspective," IEEE Trans. Net. Sci. Eng., vol. 10, no. 3, pp. 1376-1388, 2023.custom:[[[-]]]
- 169 H. Luo et al., "An energy-efficient wireless blockchainsharding scheme for pbft consensus," IEEE Trans. Network Sci. Eng., 2024.custom:[[[-]]]
- 170 H. Hu et al., "One-to-many semantic communication systems: Design, implementation, performance evaluation," IEEE Commun. Lett., vol. 26, no. 12, pp. 2959-2963, 2022.custom:[[[-]]]
- 171 J. A. Zhang et al., "An overview of signal processing techniques for joint communication and radar sensing," IEEE J. Sel. Topics Signal Process., vol. 15, no. 6, pp. 1295-1315, 2021.custom:[[[-]]]
- 172 E. Basar et al., "Wireless communications through reconfigurable intelligent surfaces," IEEE Access, vol. 7, pp. 116753-116773, 2019.custom:[[[-]]]
- 173 L. Zhao et al., "Radio resource allocation for integrated sensing, communication, and computation networks," IEEE Trans. Wireless Commun., vol. 21, no. 10, pp. 8675-8687, 2022.custom:[[[-]]]
- 174 P. Liu et al., "Vertical federated edge learning with distributed integrated sensing and communication," IEEE Commun. Lett., vol. 26, no. 9, pp. 2091-2095, 2022.custom:[[[-]]]
- 175 W. Li et al., "BC-based data security for AI applications in 6G networks," IEEE Netw., vol. 34, no. 6, pp. 31-37, 2020.custom:[[[-]]]
- 176 X. Li et al., "Energy-aware blockchain for multiple autonomous underwater vehicles cooperative operation," in CCC, 2021.custom:[[[-]]]
- 177 Y . Dai et al., "Deep reinforcement learning for resource allocation in BC-based federated learning," in Proc. IEEE ICC, pp. 179-184, 2023.custom:[[[-]]]
- 178 S. Fan et al., "Mobile devices strategies in BC-based federated learning: A dynamic game perspective," IEEE Trans. Netw. Sci. Eng., vol. 10, no. 3, pp. 1376-1388, 2023.custom:[[[-]]]
- 179 H. Luo et al., "An energy-efficient wireless blockchainsharding scheme for pbft consensus," IEEE Trans. Netw. Sci. Eng., pp. 1-12, 2024.custom:[[[-]]]
- 180 A. Sadiq et al., "BC-based data and energy trading in the internet of electric vehicles," IEEE Access, vol. 9, pp. 7000-7020, 2021.custom:[[[-]]]
- 181 W. Xiong and L. Xiong, "Data trading certification based on consortium BC and smart contracts," IEEE Access, vol. 9, pp. 3482-3496, 2021.custom:[[[-]]]
- 182 L. U. Nguyen et al., "Modeling and analysis of data trading on BCbased market in IoT networks," IEEE Internet Things J., vol. 8, no. 8, pp. 6487-6497, 2021.custom:[[[-]]]
- 183 S. Sun et al., "BC-based IoT access control system: Towards security, lightweight, and cross-domain," IEEE Access, vol. 9, pp. 36868-36878, 2021.custom:[[[-]]]
- 184 V . Y . Kemmoe et al., "Recent advances in smart contracts: A technical overview and state of the art," IEEE Access, vol. 8, pp. 117782-117801, 2020.custom:[[[-]]]
- 185 E. A. Shammar et al., "A survey of IoT and BC integration: Security perspective," IEEE Access, vol. 9, pp. 156114-156150, 2021.custom:[[[-]]]
- 186 P. P. Ray et al., "BC for IoT-based healthcare: Background, consensus, platforms, and use cases," IEEE Syst. J., vol. 15, no. 1, pp. 85-94, 2021.custom:[[[-]]]
- 187 K. Gilani et al., "A survey on BC-based identity management and decentralized privacy for personal data," Proc. BRAINS, pp. 97-101, 2020.custom:[[[-]]]
- 188 P. Gururaj, "Identity management using permissioned BC," in Proc. ICOMBI, pp. 1-3, 2020.custom:[[[-]]]
- 189 R. T. Moreno et al., "A trusted approach for decentralized and privacy-preserving identity management," IEEE Access, vol. 9, pp. 105788-105804, 2021.custom:[[[-]]]
- 190 A. Yazdinejad et al., "An energy-efficient sdn controller architecture for IoT networks with BC-based security," IEEE Trans. Services Comput., vol. 13, no. 4, pp. 625-638, 2020.custom:[[[-]]]
- 191 H. M. Abdullah, A. Gastli, and L. Ben-Brahim, "Reinforcement learning based ev charging management systems—a review," IEEE Access, vol. 9, pp. 41506-41531, 2021.custom:[[[-]]]
- 192 A. Rahman et al., "Smart block-sdn: An optimized BC-sdn framework for resource management in IoT," IEEE Access, vol. 9, pp. 28361-28376, 2021.custom:[[[-]]]
- 193 T. Wang et al., "Game-theoretical analysis of mining strategy for bitcoin-ng BC protocol," IEEE Syst. J., vol. 15, no. 2, pp. 2708-2719, 2021.custom:[[[-]]]
- 194 P. Haridas et al., "Code characterization with graph convolutions and capsule networks," IEEE Access, vol. 8, pp. 136307-136315, 2020.custom:[[[-]]]